Microsoft Azure Active Directory - OLD
About
Azure Active Directory (Azure AD) is Microsoft's cloud-based identity and access management service, which allows employees to sign in and access internal and external resources.
Why You Should Integrate
Integrating with a Directory Service like Microsoft Azure Active Directory will provide visibility and device presence awareness for an environment.
How Does the Integration Work
This integration pulls device objects from Azure AD that are either joined or registered to the domain. This can be controlled by identifying the TrustType Sevco will filter in or out within the configuration. By default, this integration will collect all three trustTypes but will not collect empty trustTypes. An empty trustType implies the device record comes from InTune, which is reported by the Microsoft InTune source.
This data is only used internally; we do not share it with any parties outside of Sevco. Refer to our privacy policy for details.
Configuration
-
Choose a Schema: A schema is a configuration template that defines a specific way to connect, authenticate, and interact with a source. The following are the available schemas
- OAuth2 with asset filtering: Will retrieve computer objects using OAuth2 authentication. Note: OAuth2 will require re-authentication every 90 days, requiring you to edit and re-activate the source.
- Client ID/Secret with asset filtering: Will retrieve computer objects using a client ID/secret.
-
Configure plugin: Configure the plugin with the required fields.
OAuth2 with asset filtering
Field | Description | Example |
|---|---|---|
Include bring your own personal device | If selected will retrieve devices registered in Azure AD with a trustType of Workplace | n/a |
Include cloud only joined devices | If selected will retrieve devices joined to Azure AD with a trustType of AzureAd | n/a |
Include on-premises domain joined devices joined to Azure AD | If selected will retrieve devices in Hybrid Azure AD with a trustType of ServerAd | n/a |
Client ID/Secret with asset filtering
Field | Description | Example |
|---|---|---|
| The Application (client) ID of the app created for access. |
|
| The Directory (tenant) ID of the associated domain |
|
| The value of the app's client secret created to authenticate with the source. |
|
Include bring your own personal device | If selected will retrieve devices registered in Azure AD with a trustType of Workplace | n/a |
Include cloud only joined devices | If selected will retrieve devices joined to Azure AD with a trustType of AzureAd | n/a |
Include on-premises domain joined devices joined to Azure AD | If selected will retrieve devices in Hybrid Azure AD with a trustType of ServerAd | n/a |
-
If you chose OAuth2 with asset filtering, log in with your Microsoft credentials and accept the permission request.
-
Configure Name: OPTIONAL: You can give the configuration a name to provide an identifiable attribute of the configuration to delineate other similar configurations.
-
Activate Config: To enable this configuration and begin pulling data select "Activate". If you wish to save the configuration to come back later to finish, select "Save Draft". This will save the configuration, but keep it disabled until Activated.
Source Documentation
Creating credentials
You'll be asked to provide source credentials that Sevco will use to connect to MS Azure AD.
OAuth2 with asset filtering
Use an existing MS Azure AD account with admin permissions authorized to grant permissions defined in the Required Permissions - OAuth2 with asset filtering section below.
Client ID/Secret with asset filtering
You'll be asked to provide a client secret that Sevco will use to connect to Microsoft Azure AD. This will require the creation of an application in Azure in order to provide API-based access. The following steps will walk you through creating a registered application and identify the necessary values to record for configuration. (Microsoft Documentation: Tutorial: Register an app with Azure Active Directory)
- Go to Azure Active Directory > App registrations*
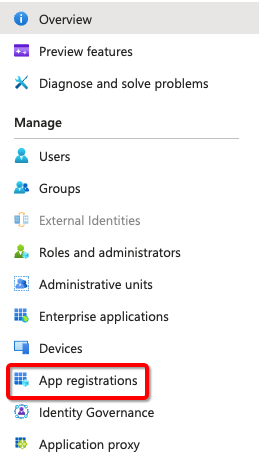
- Create a new registration
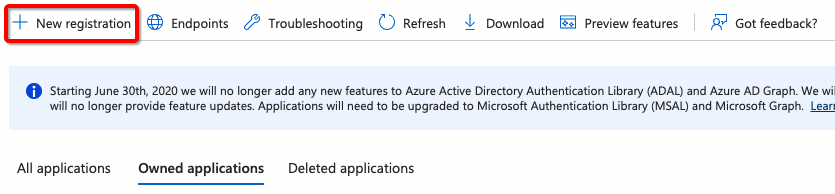
- Give the app a user-friendly name and click
Register
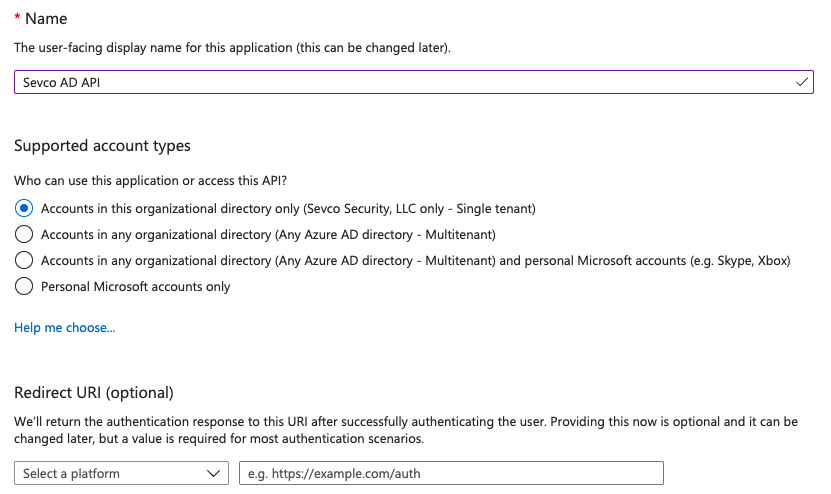
- Obtain the Application (client) ID and Directory (tenant) ID for configuring the source.

- Obtain a secret by going to Certificates and secrets
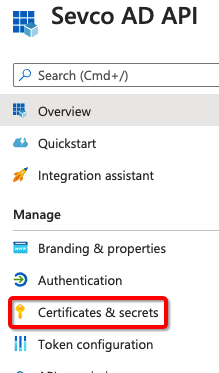
- Generate New client secret
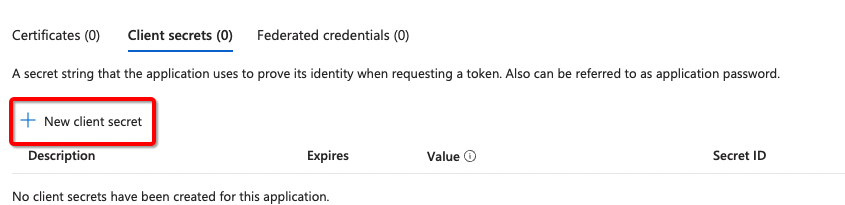
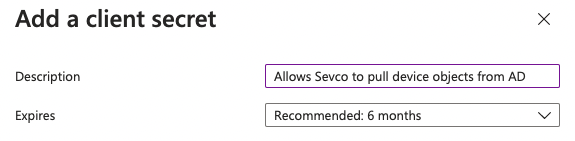
- Give the secret a Description and expiration that follows your password rotation policy.
- Obtain (copy) the Client secret value
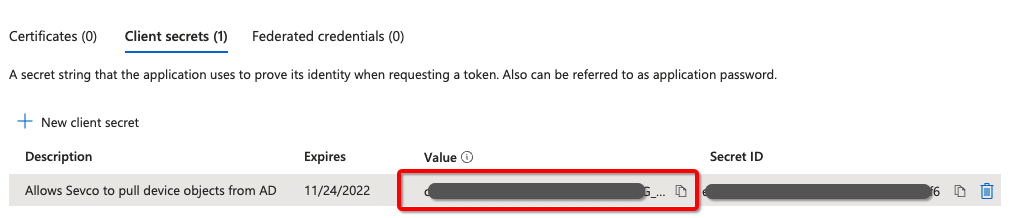
NOTE: Ensure to input the App SecretValue, not the Secret ID when configuring the plugin.
- Add the appropriate permissions by following the steps in Required Permissions - Client ID/Secret with asset filtering below.
Required Permissions
OAuth2 with asset filtering
The OAuth authentication flow will ask the user to authorize Sevco access by requesting the following permissions
- Type: Application permissions
- Device.Read.All
<REVIEW>
Client ID/Secret with asset filtering
The configured app will require the following permissions
- Type: Application permissions
- Permission: Device.Read.All
The following steps will walk you through configuring the proper permissions
- *Go to Azure Active Directory > App registration
- Select the application created for Sevco when following the steps inCreating credentials - Client ID/Secret with asset filtering.

NOTE: Depending on who created the application, it could be present in All applications or Owned applications
- Go to API Permissions
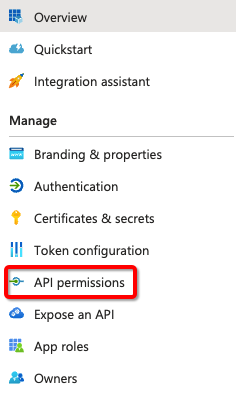
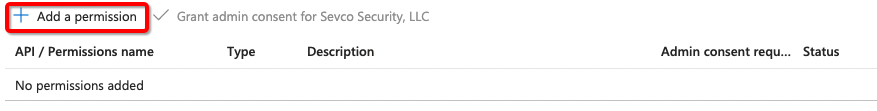
- Add a permission
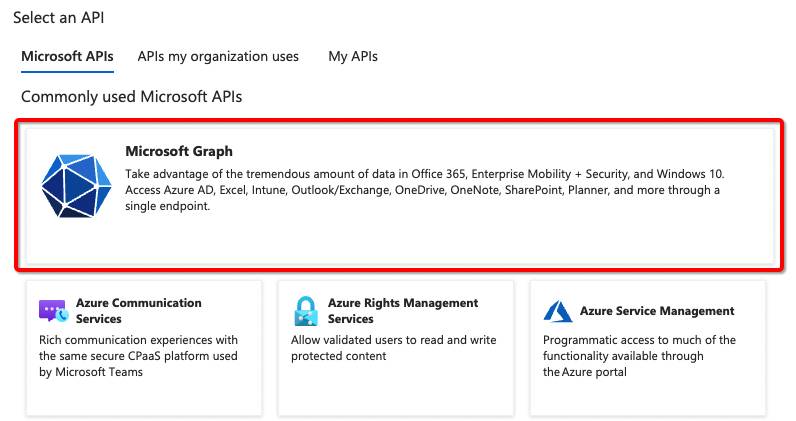
- Select Microsoft Graph and add a Delegated permission
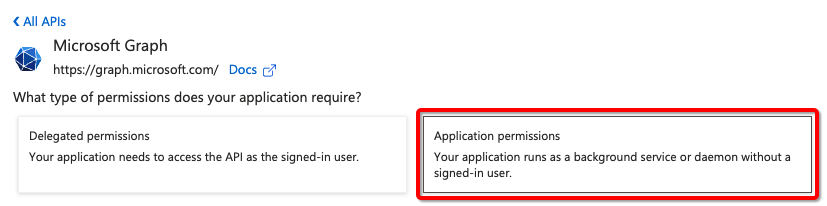
- Check Device.Read.All and click
Add permissions
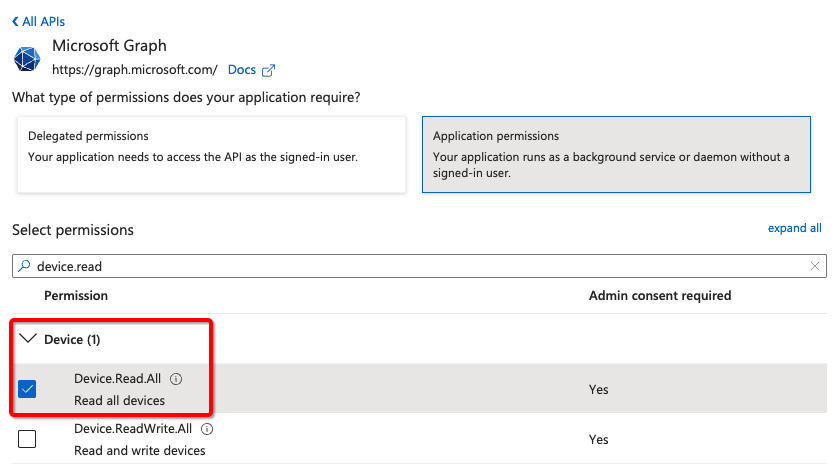
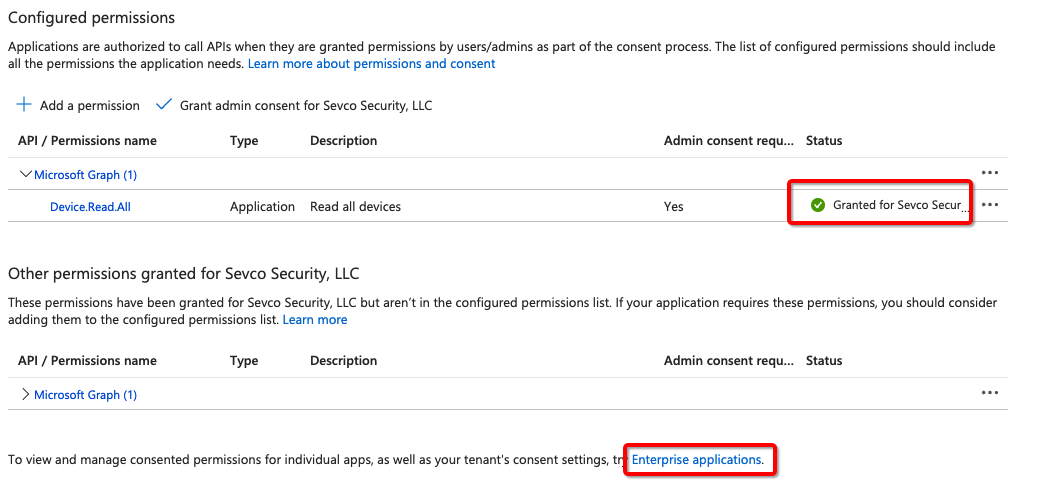
- Admin consent will be required. Grant the permissions by going to the Enterprise applications or requesting an admin to approve the request.
API Documentation
Contact Us
If you're having problems integrating a source, or if you've found something wrong in this document, please email us at [email protected].
Tags: cloud, directory service
Updated 11 months ago
