Setting Up Multi-Factor Authentication
Overview
Admin users can no longer enforce MFA Enrollment requirements for individual users; however, they can enforce MFA Enrollment at the organizational level for all members.
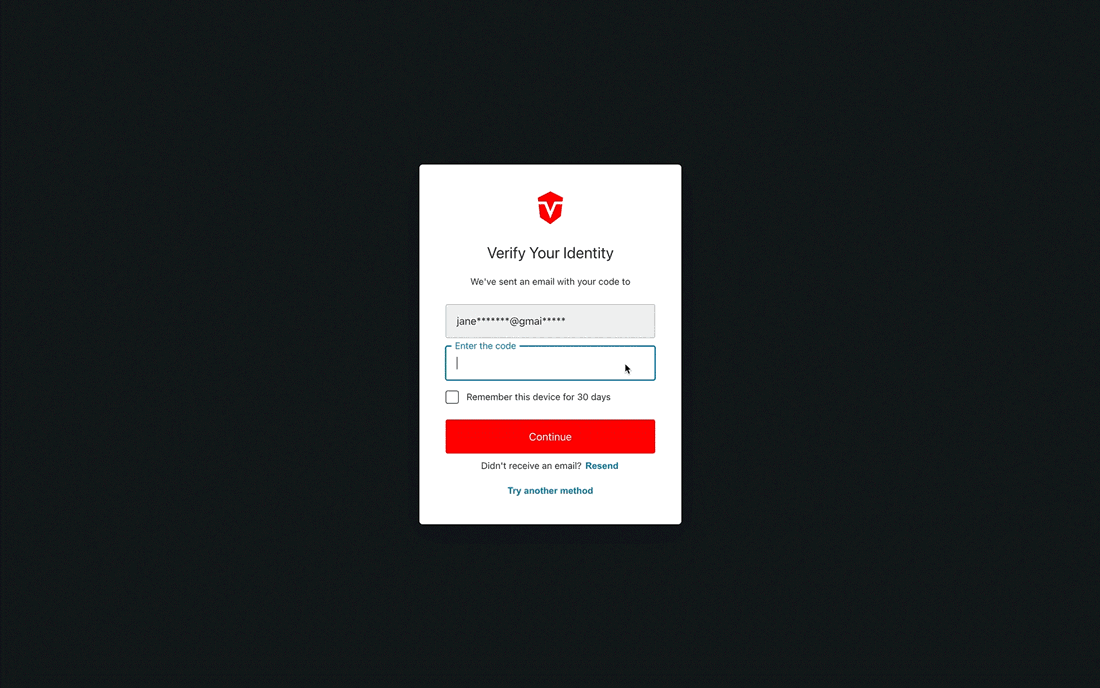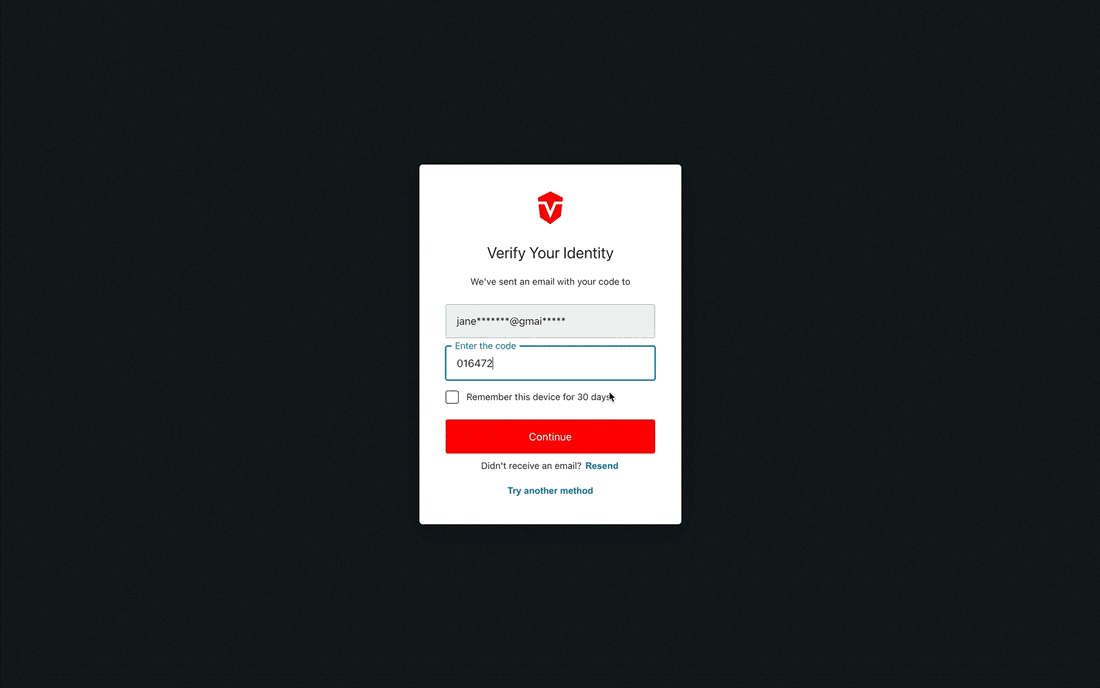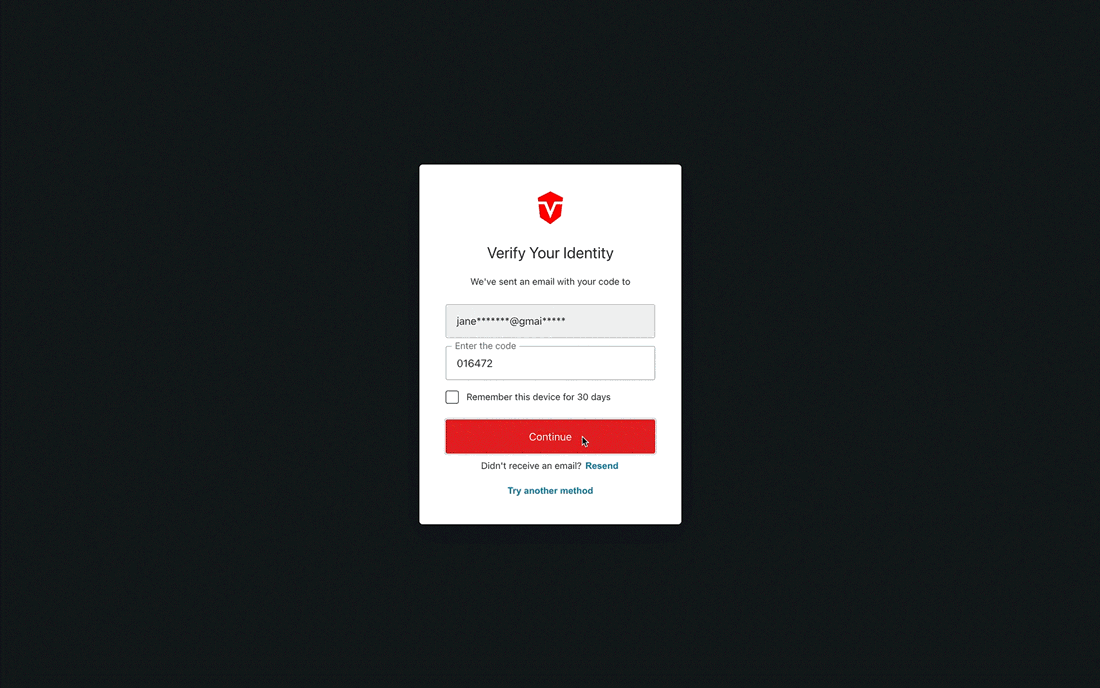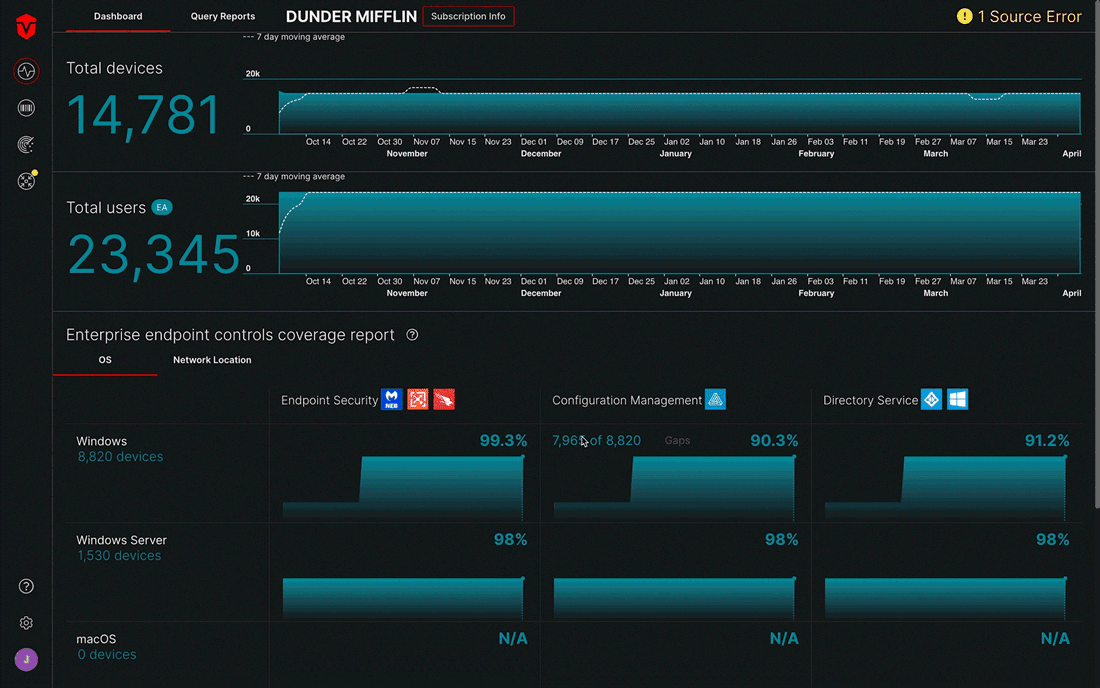
Multi-Factor Authentication (MFA) provides an additional layer of security by generating a one-time code that users must enter during sign in. If you are prompted to set up MFA while activating your account, you can do so using any QR-code-based authenticator app (i.e.Google or Microsoft Authenticator).
Enabling MFA For Your Account
MFA settings are located in the Profile page for your account. This page can be accessed by selecting the Profile icon (![]() ) at the very bottom of the Navigation bar, then selecting the Profile link from the dropdown menu.
) at the very bottom of the Navigation bar, then selecting the Profile link from the dropdown menu.
Please note that Profile icons vary in appearance from account to account. While its color is assigned at random, the icon will always contain the first letter of the first name associated with your account.
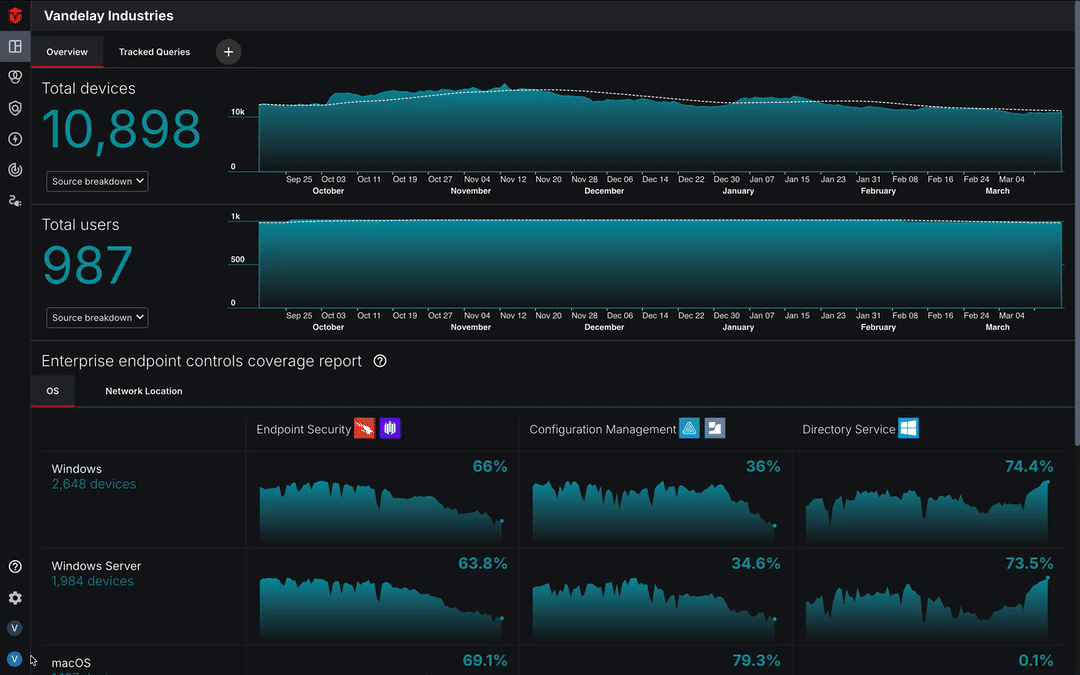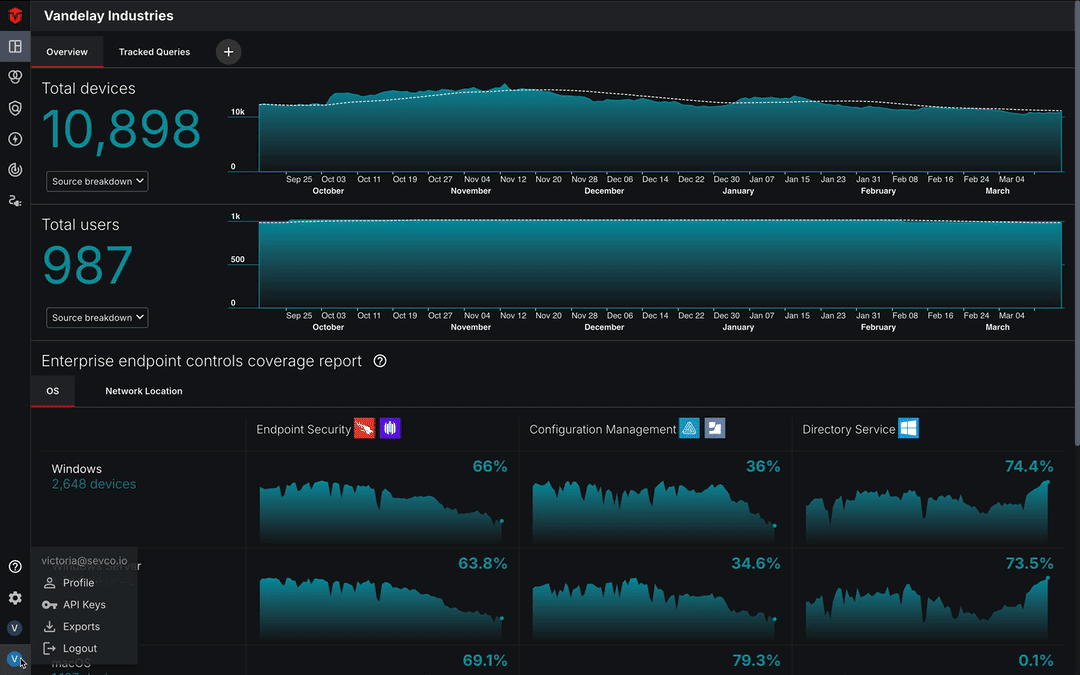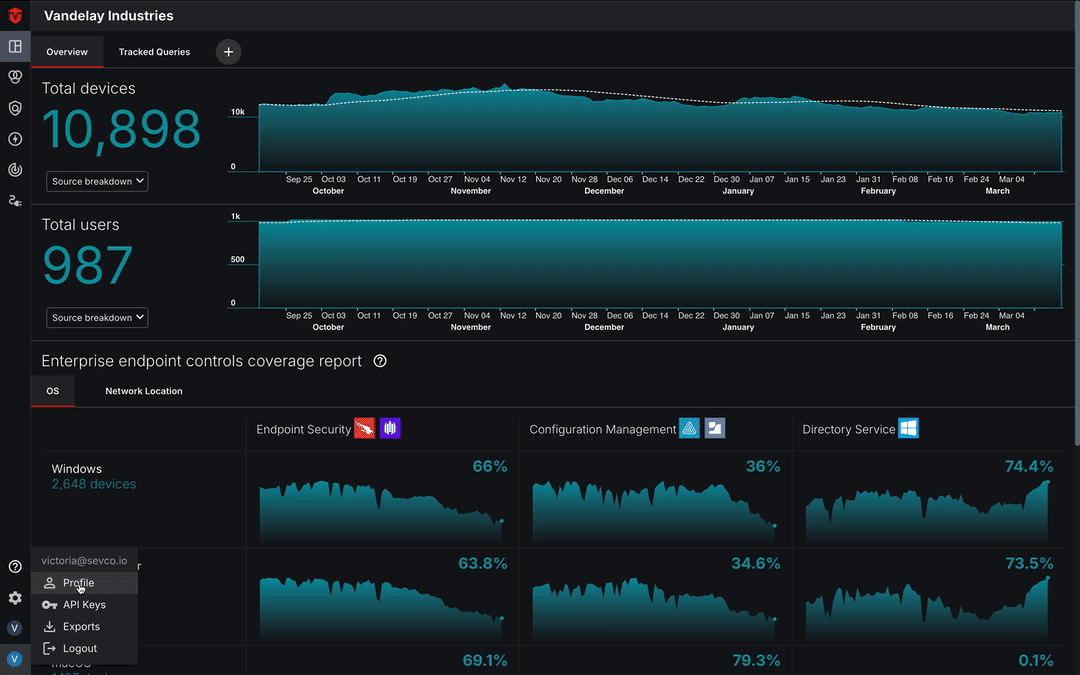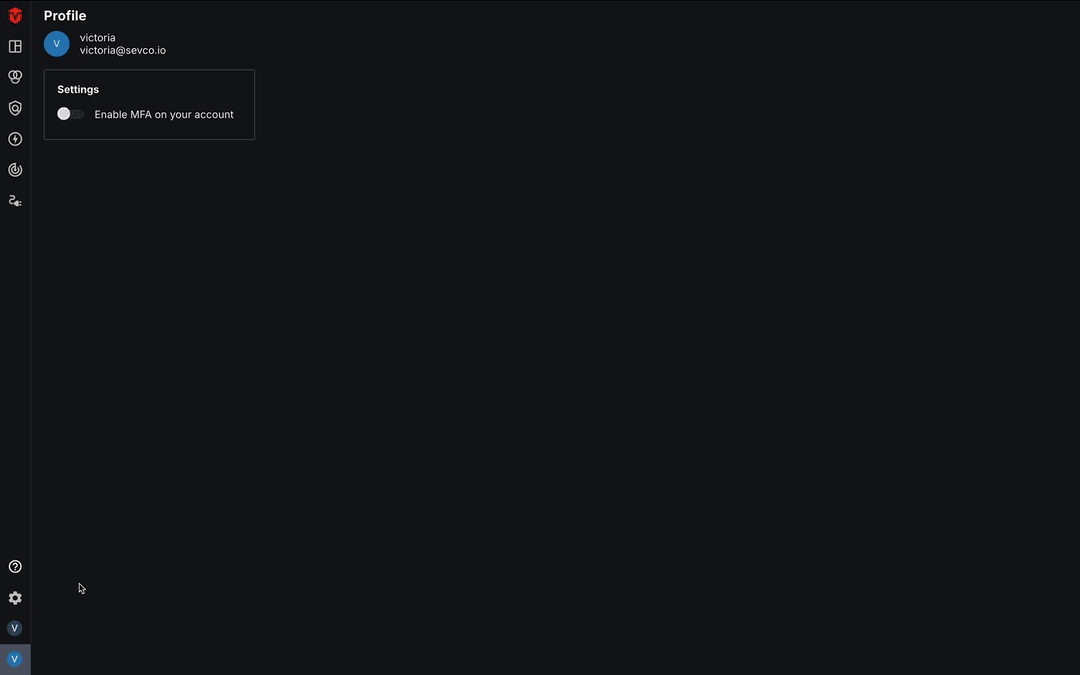
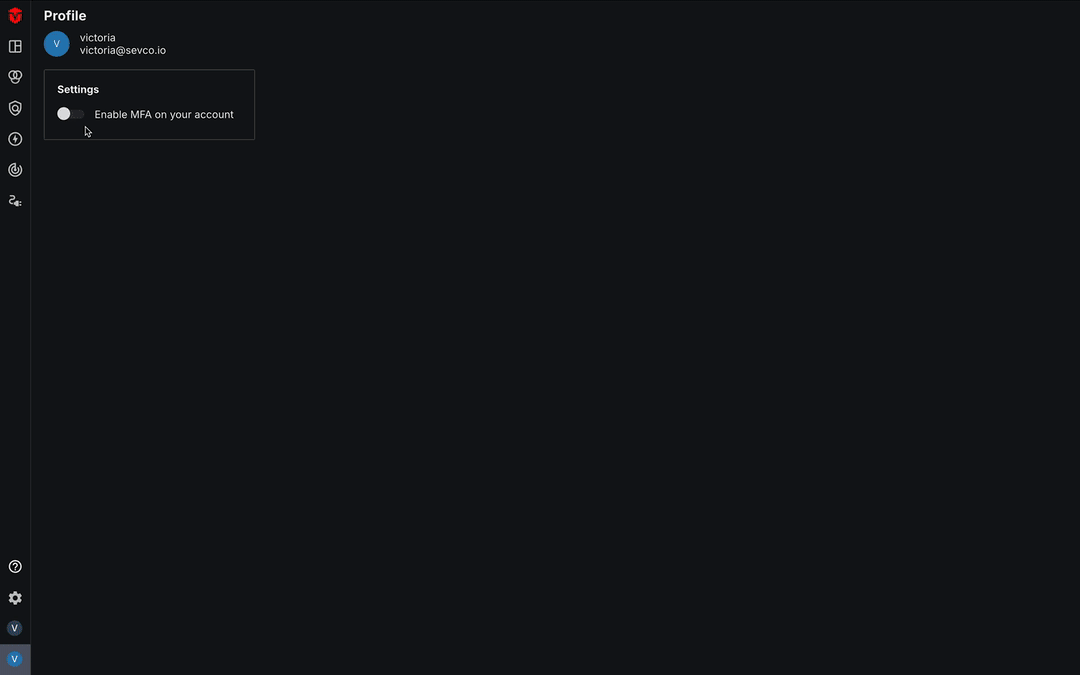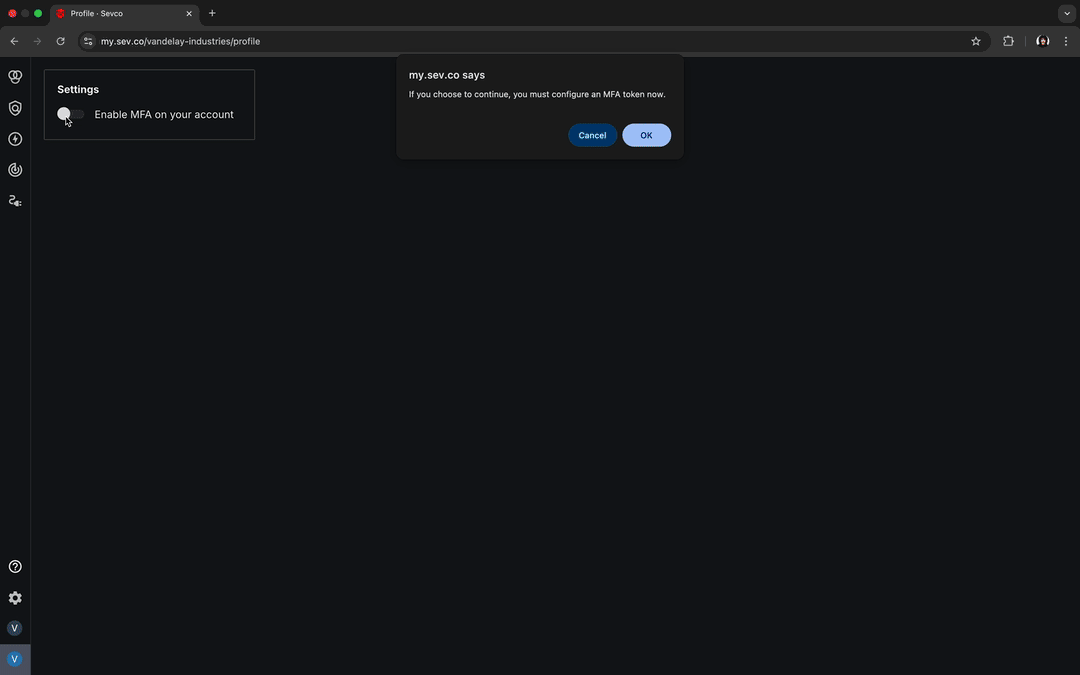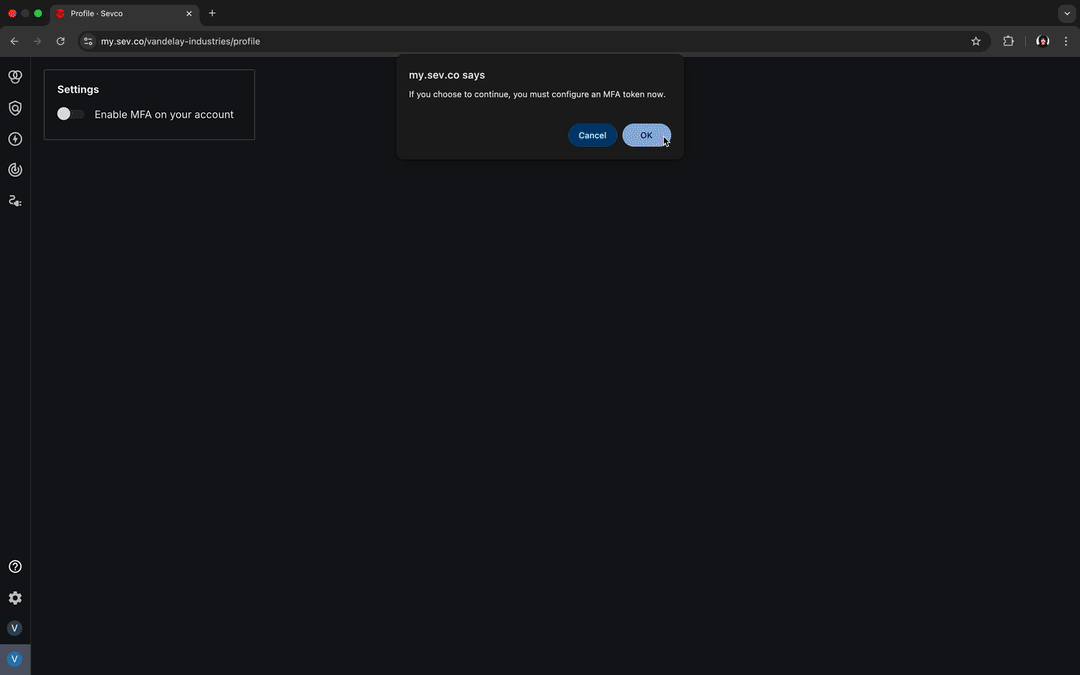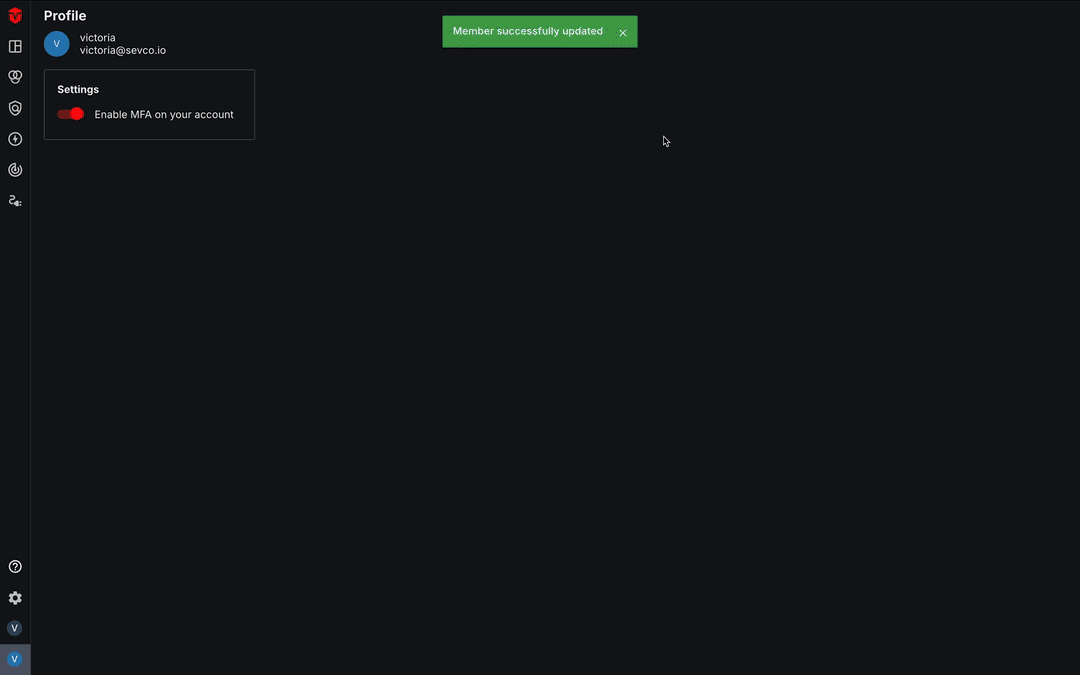
From the Profile page, select the Enable MFA on your account toggle located in the Settings panel.
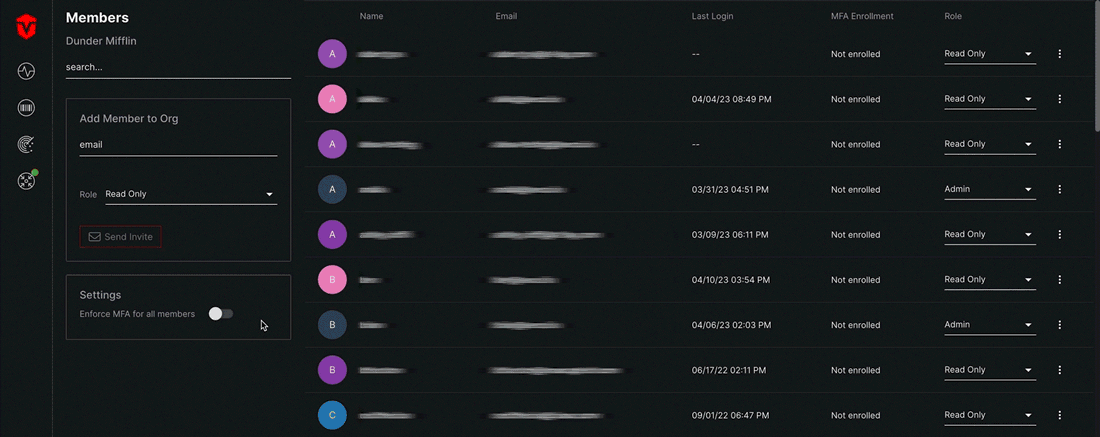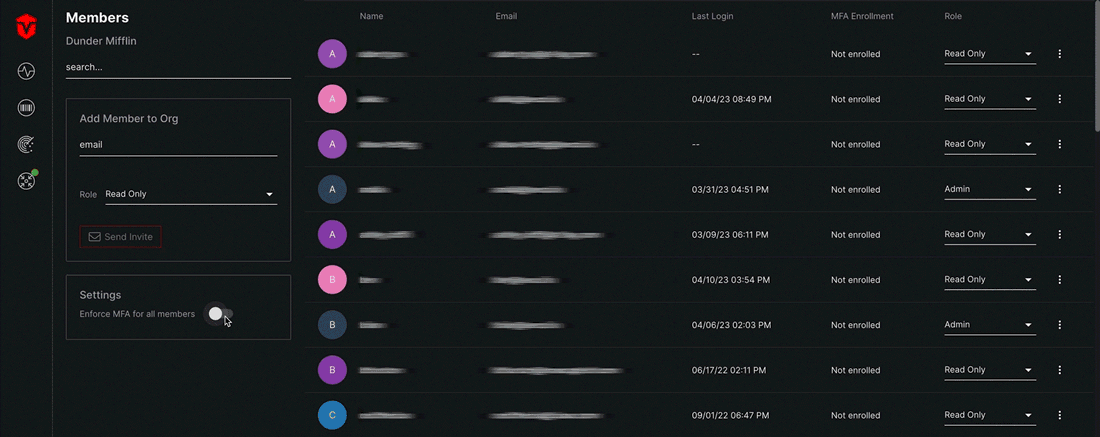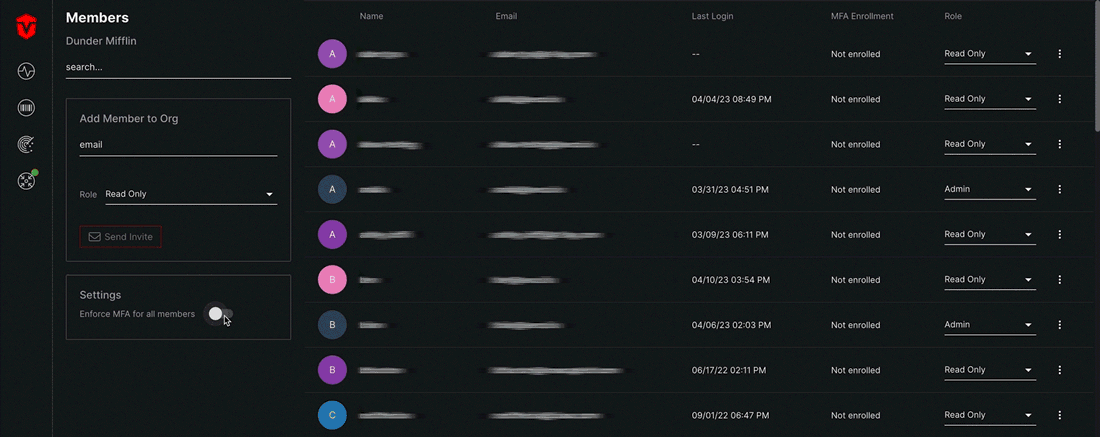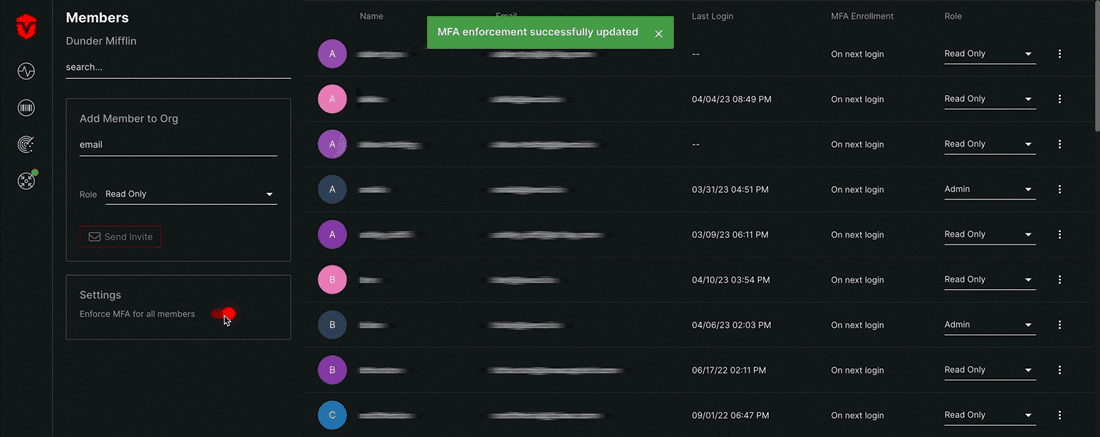
A popup will appear asking you to confirm that you would like to continue. Select OK to confirm. A green Member successfully updated message will appear and you will be redirected to the MFA Setup page.
Once you have been redirected, you will see a QR Code. Scan this code with your preferred authenticator app. Next, enter the one time code generated by the authenticator into the provided field, then click the Continue button.
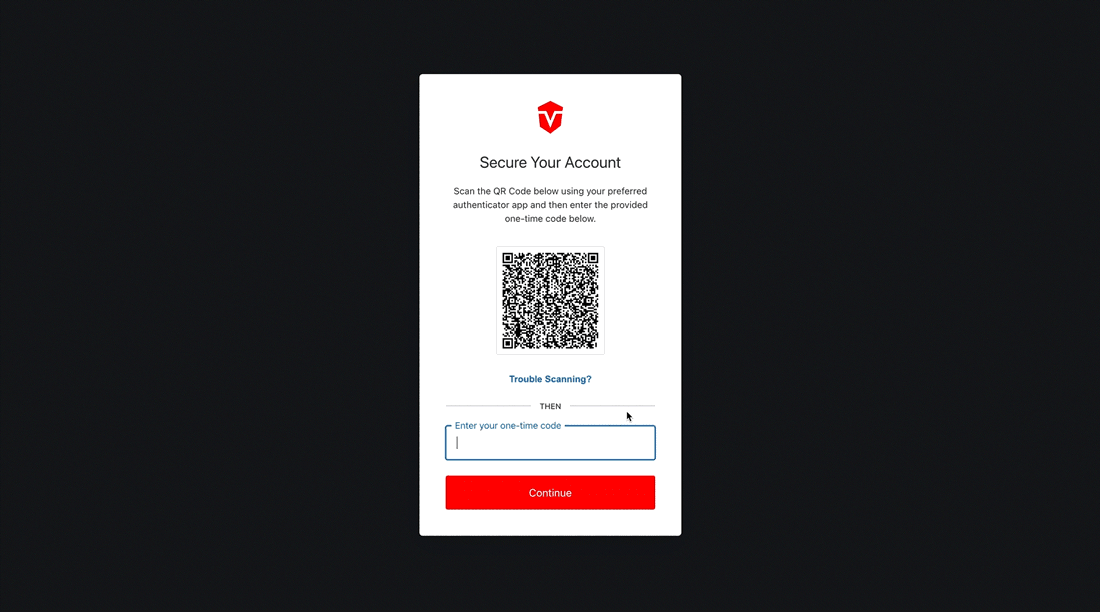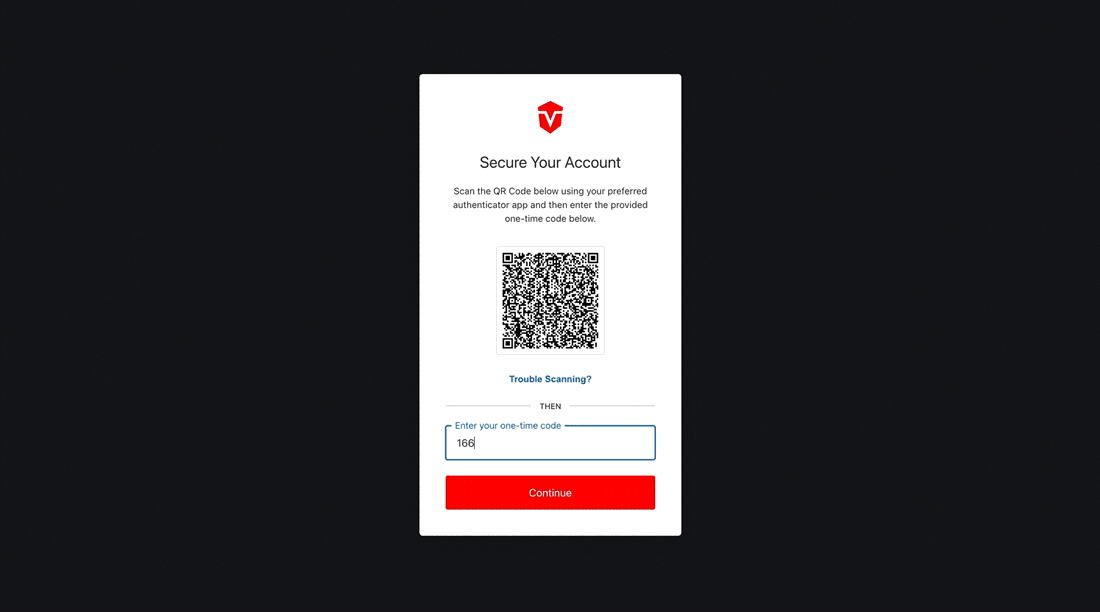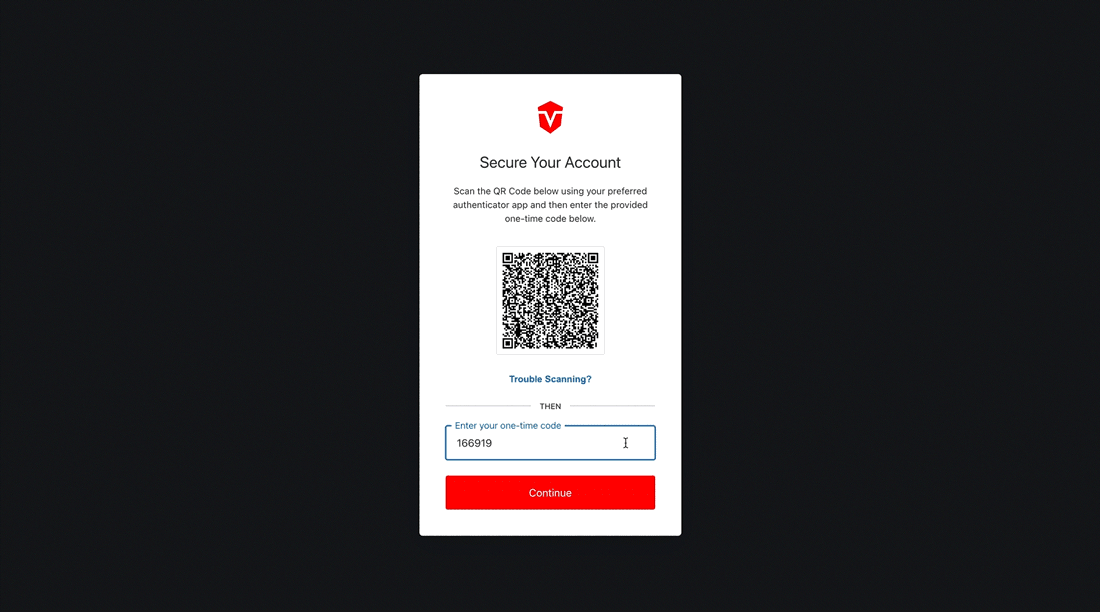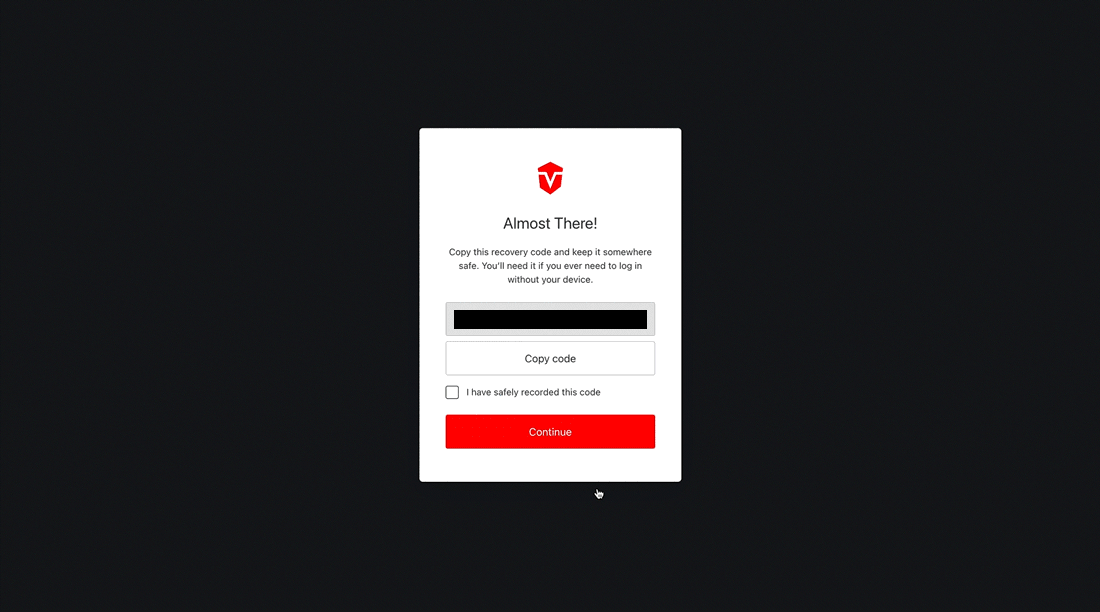
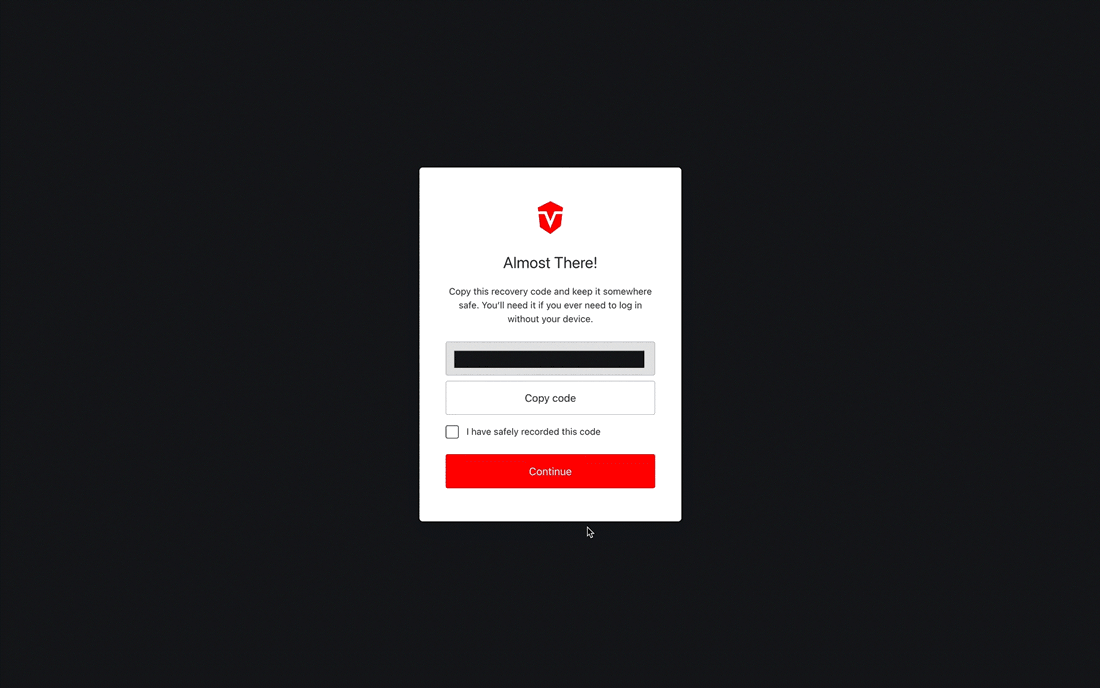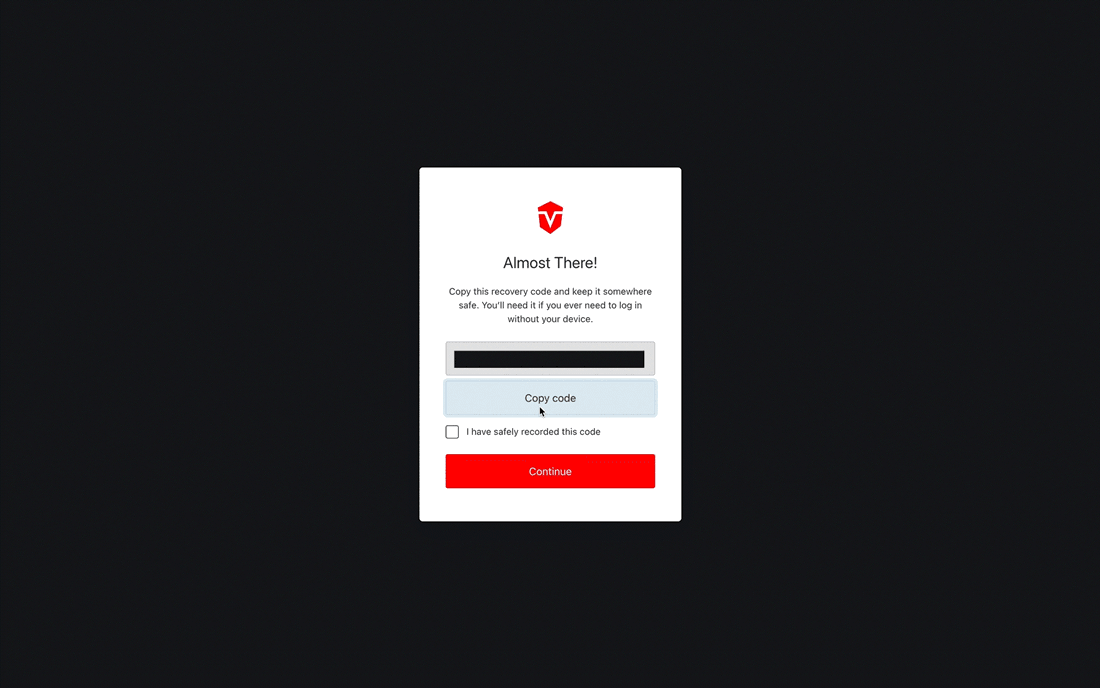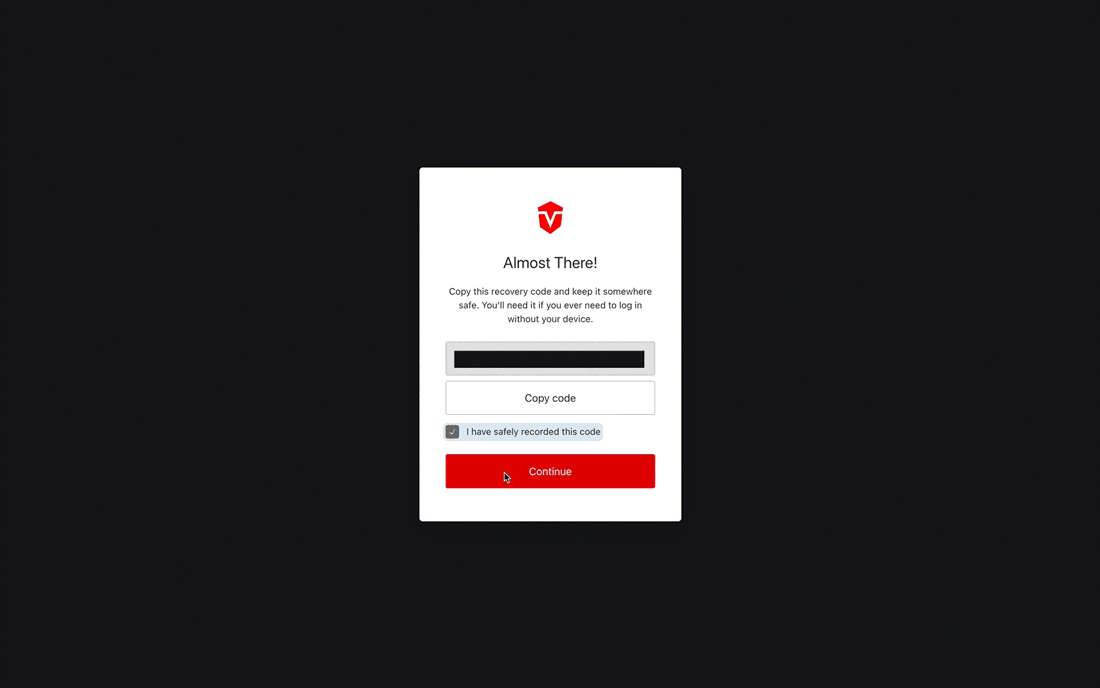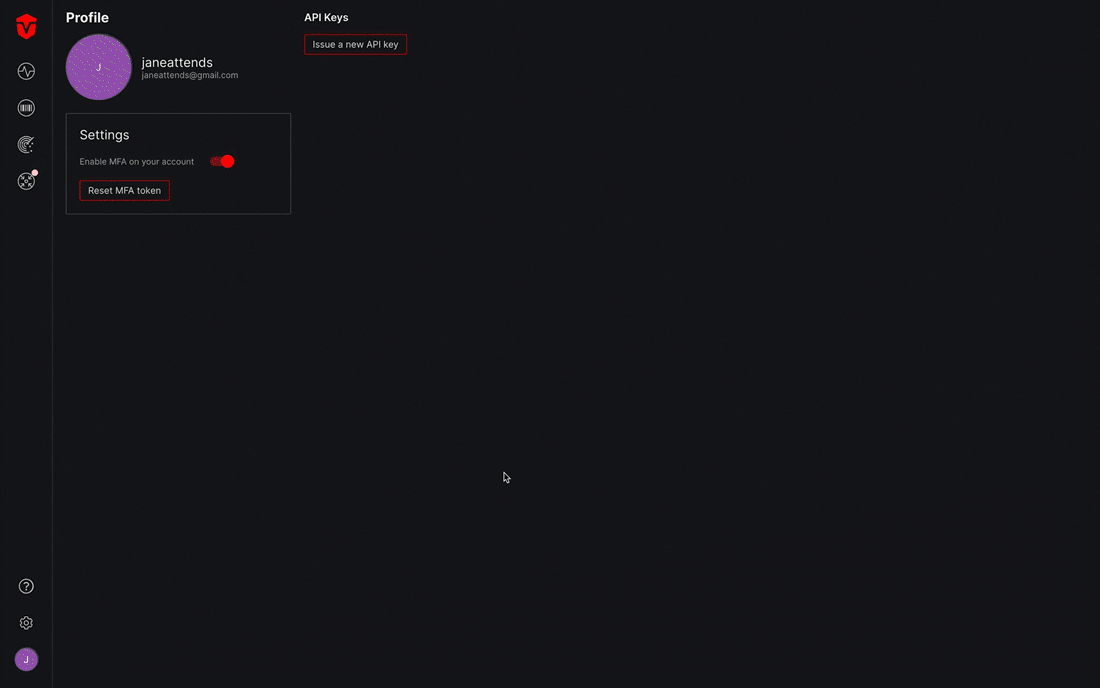
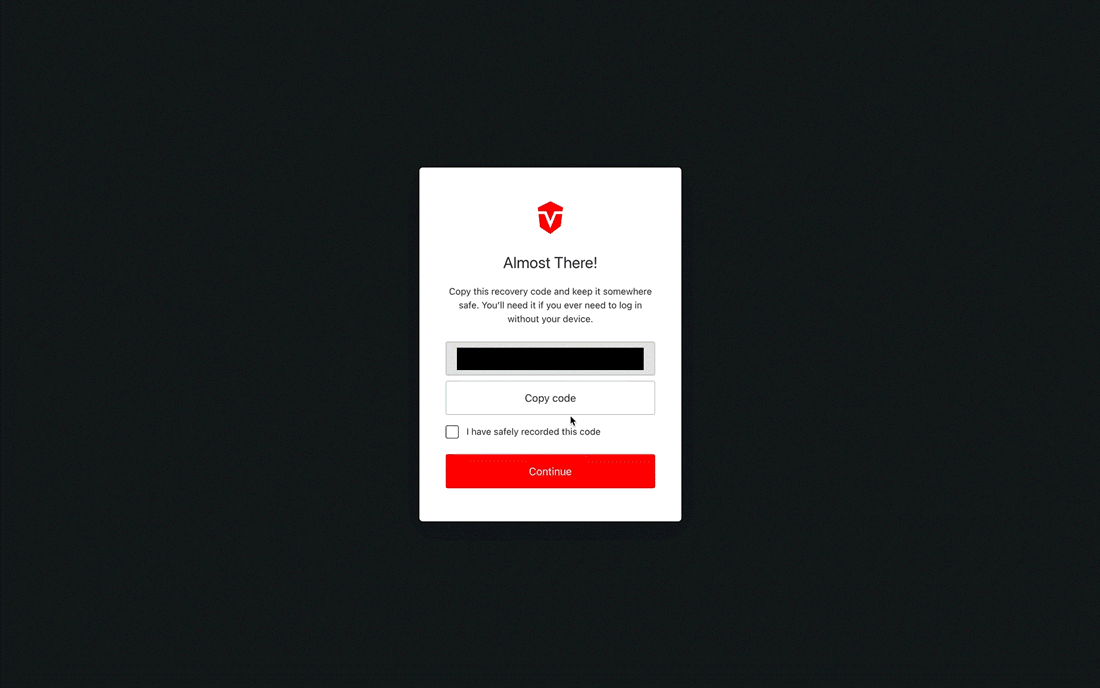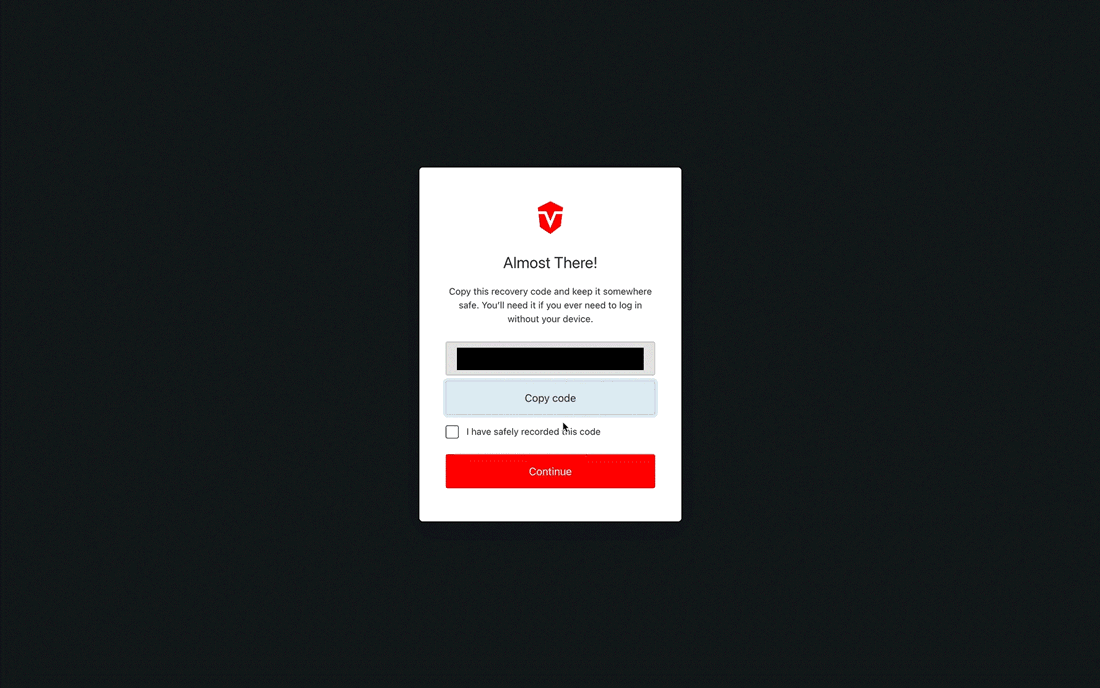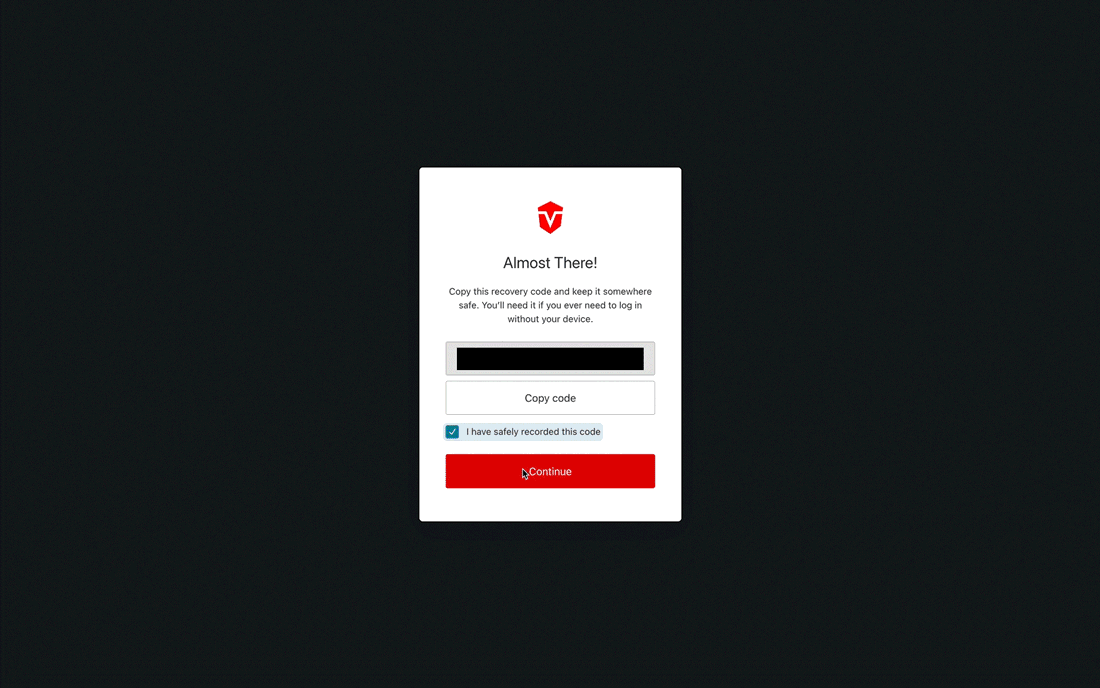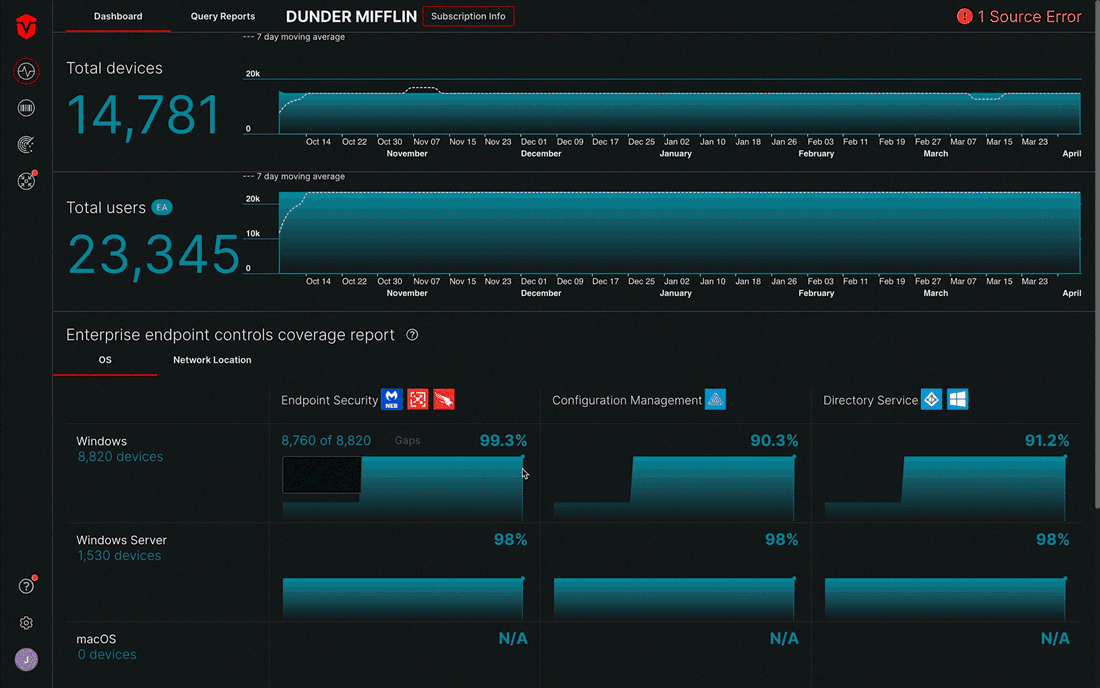
Recovery codes are only shown once and must be saved in a secure place!
You will be provided with a recovery code that can be used to log into your account in the event that you lose access to your authenticator app. Select the Copy code button to copy the code to your clipboard then save it in a secure place.
Once you've saved your code, check the I have safely recorded this code checkbox, then click the Continue button to complete this process.
Resetting an MFA Token
Note: Admin users cannot reset their own MFA Tokens and should reach out to another Admin in their organization to do so for them. If there is no other Admin user in your organization, please reach out to your CSM for assistance.
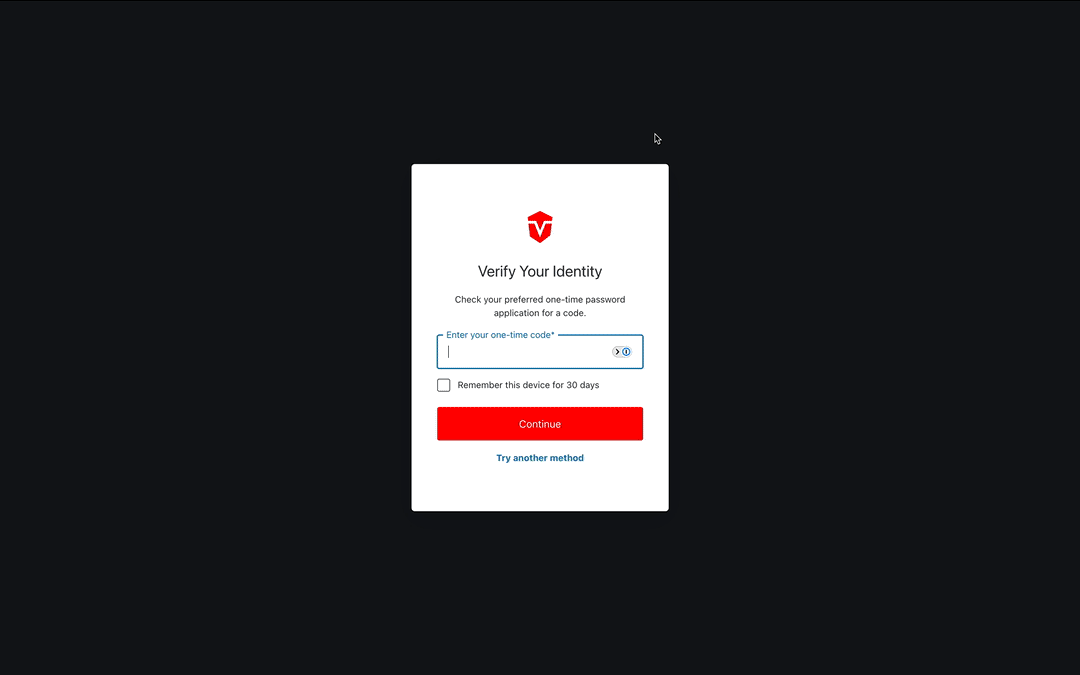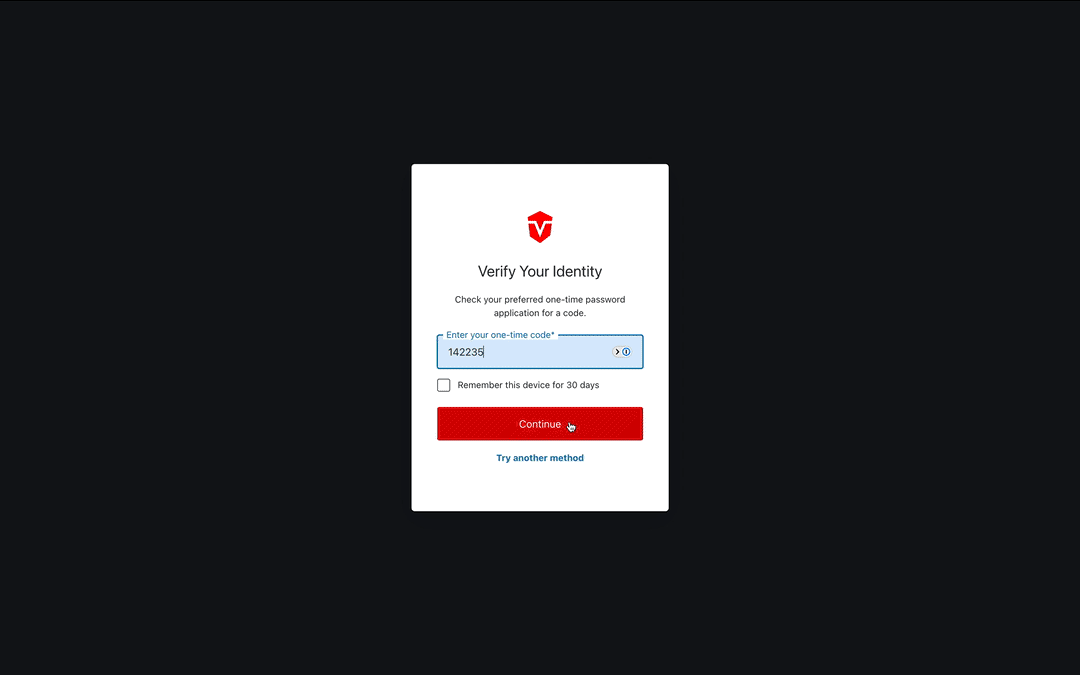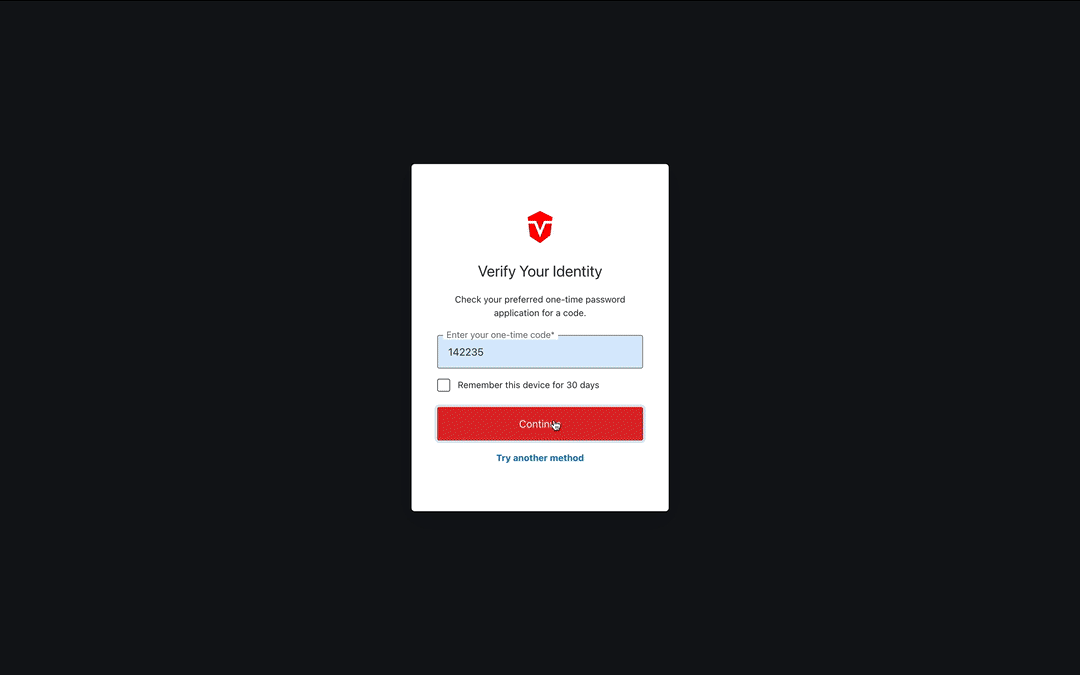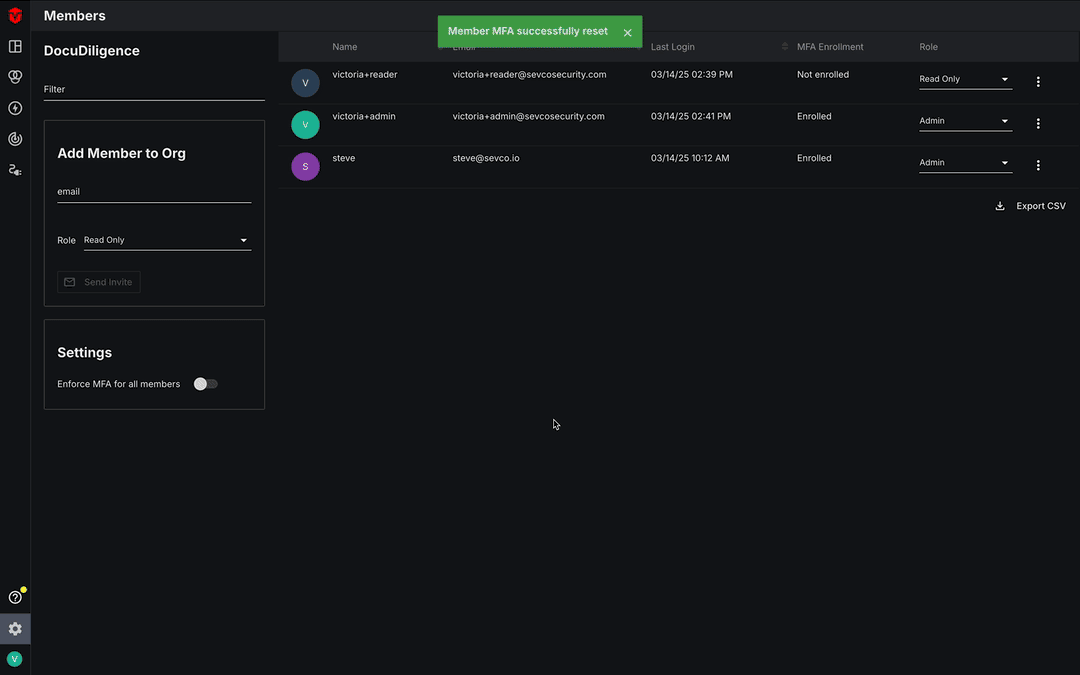
The Sevco platform allows Admin users to reset MFA Tokens for other members in their organization.
MFA tokens may be reset:
- To practice good security hygiene. Like updating your password, resetting an MFA Token can help shield you from cyber attacks
- If a user has lost access to their authenticator app.
- If you have reason to believe that a user's password or recovery code has been wrongfully obtained
Note: this page is only accessible to Admin users. If your account is Read Only, you will need to contact an Admin to view it.
Start by navigating to the Members page. This page can be accessed by clicking the Admin icon (![]() ) on the Navigation bar then select the Members link from the dropdown menu.
) on the Navigation bar then select the Members link from the dropdown menu.
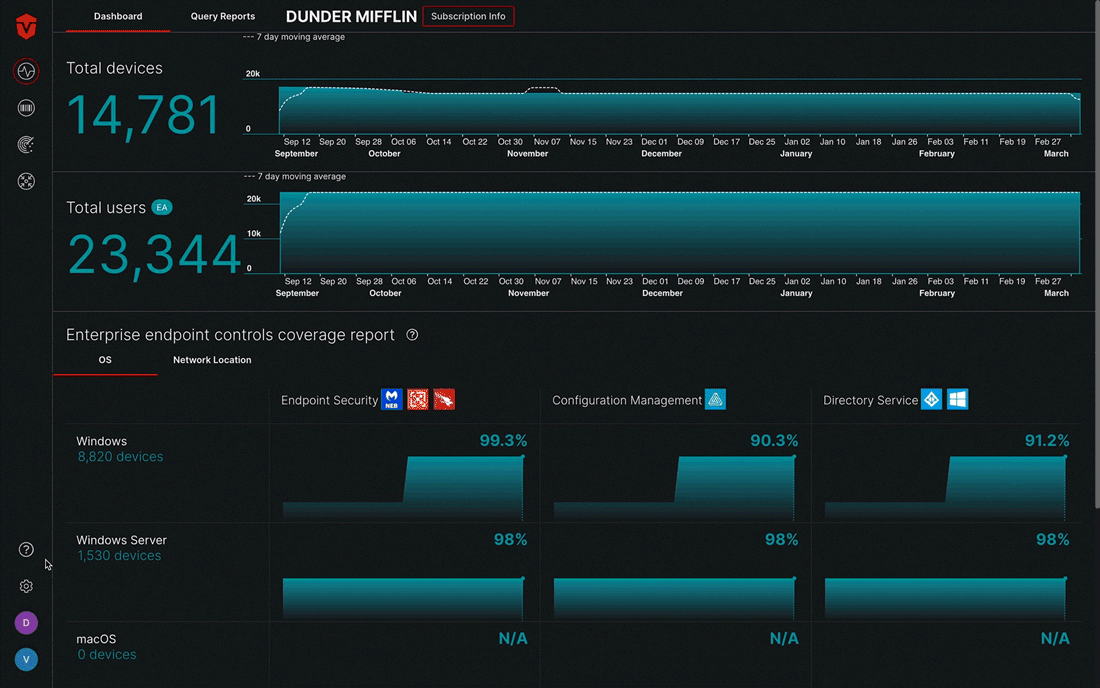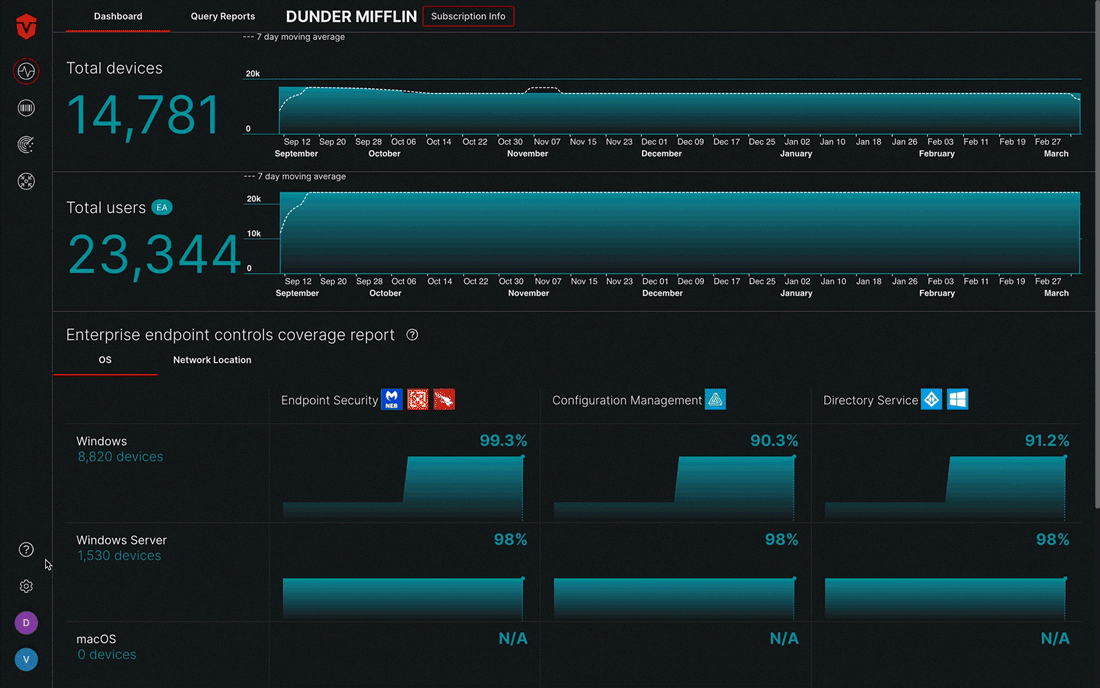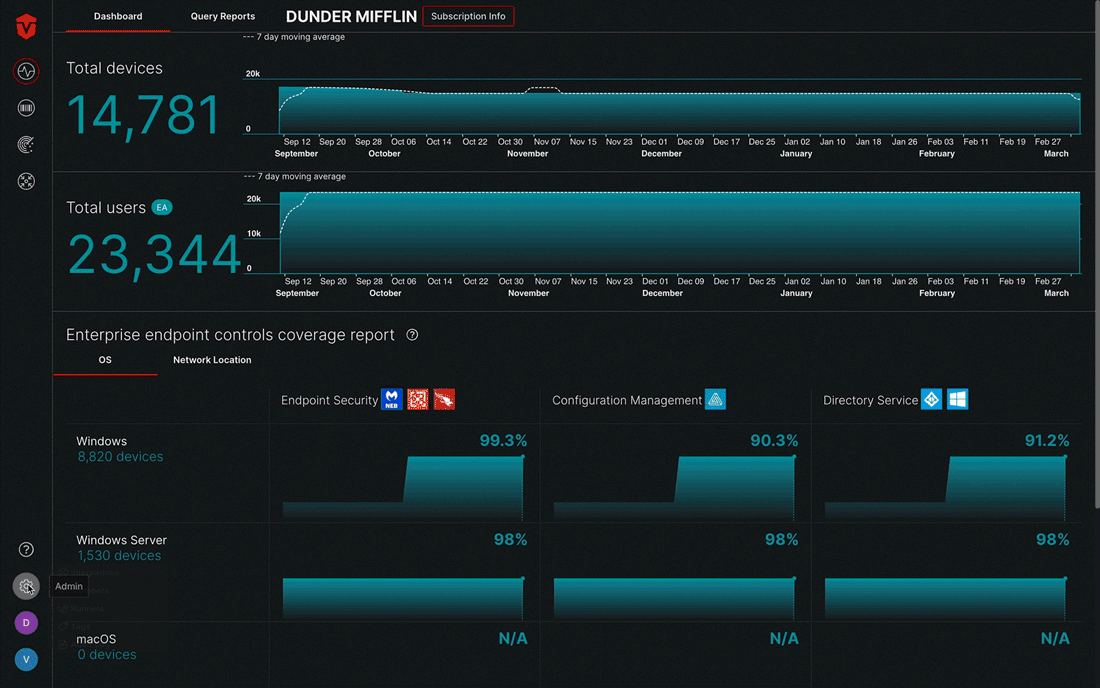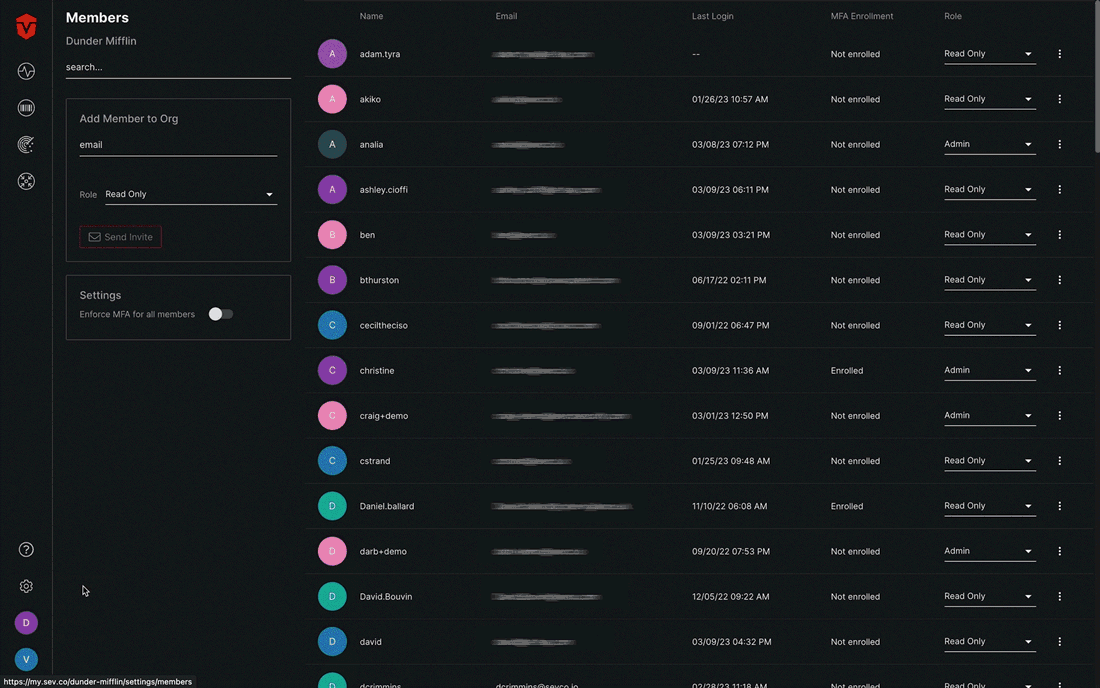
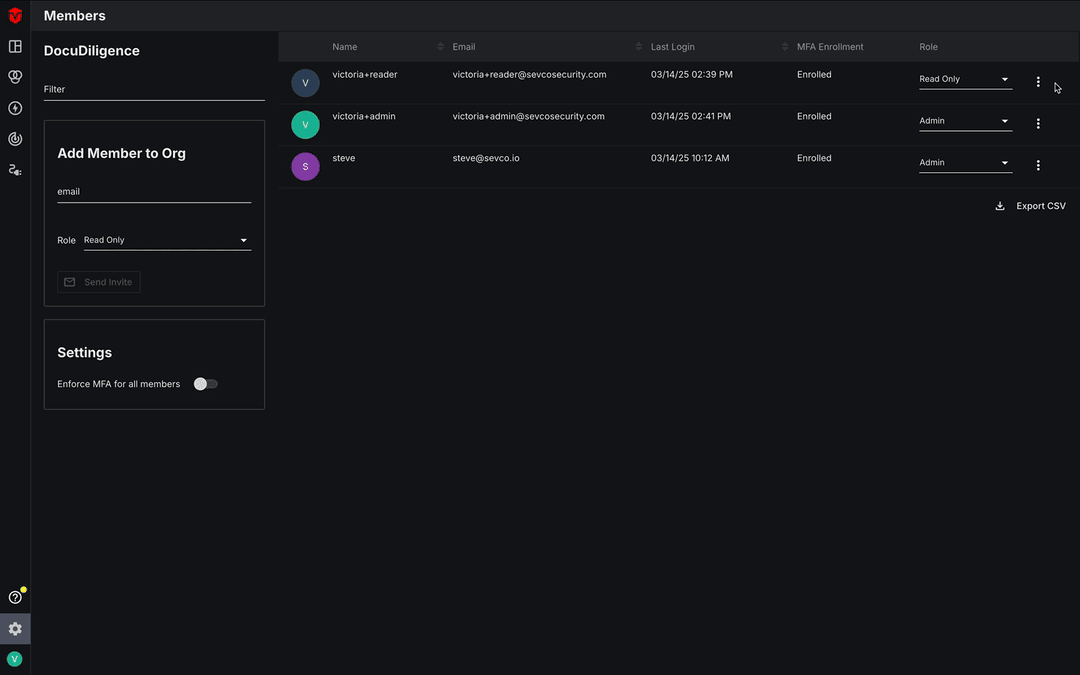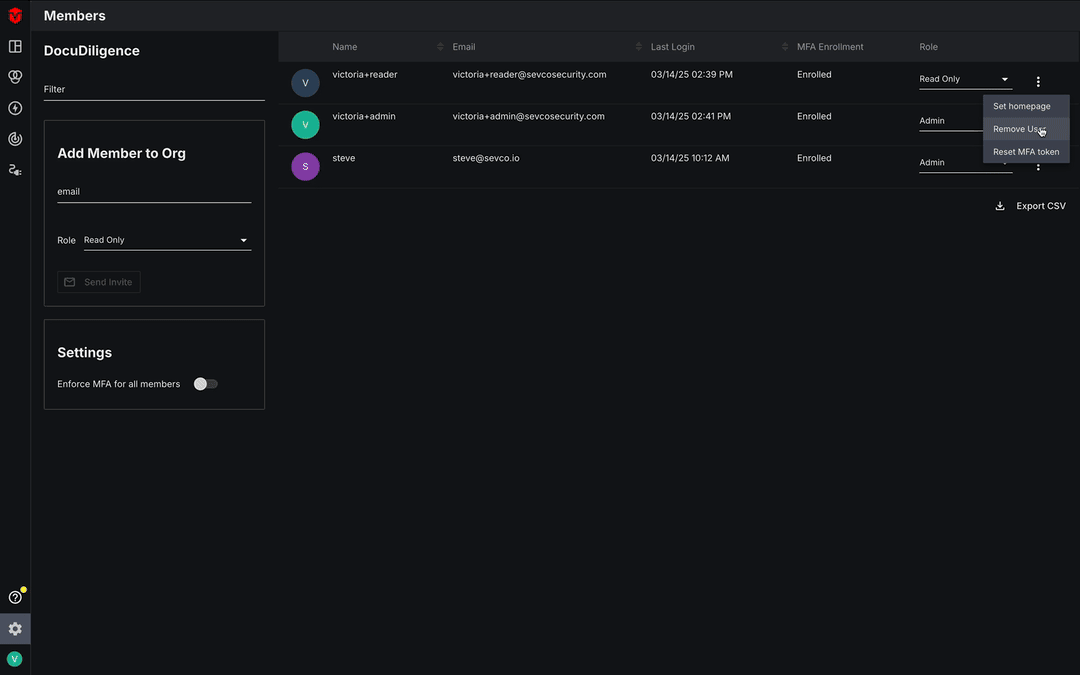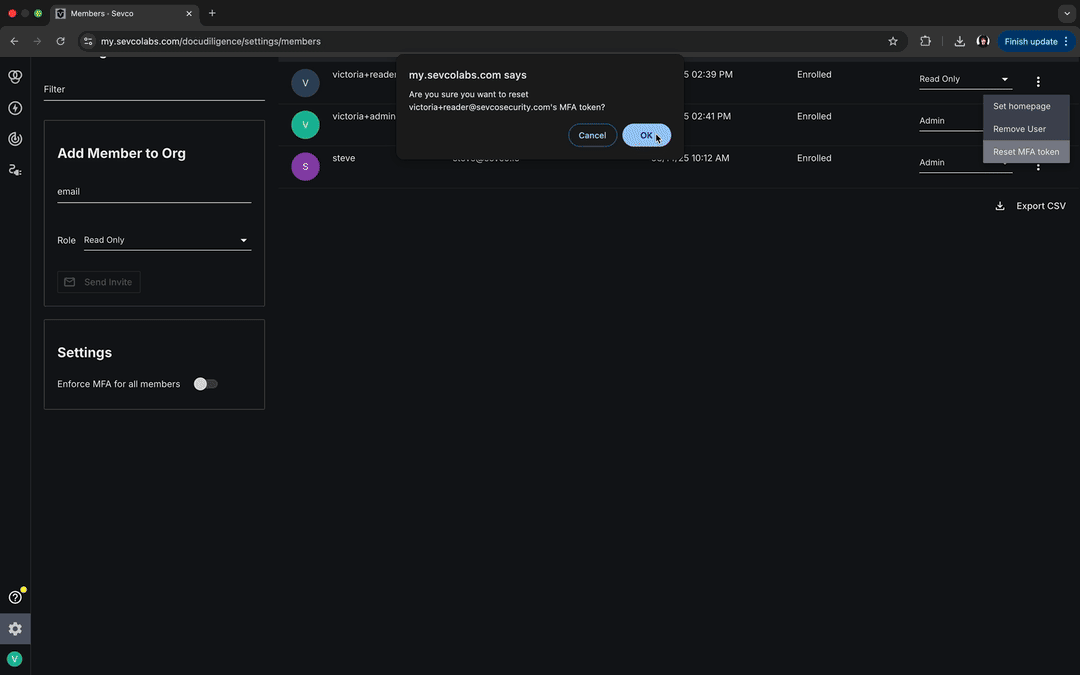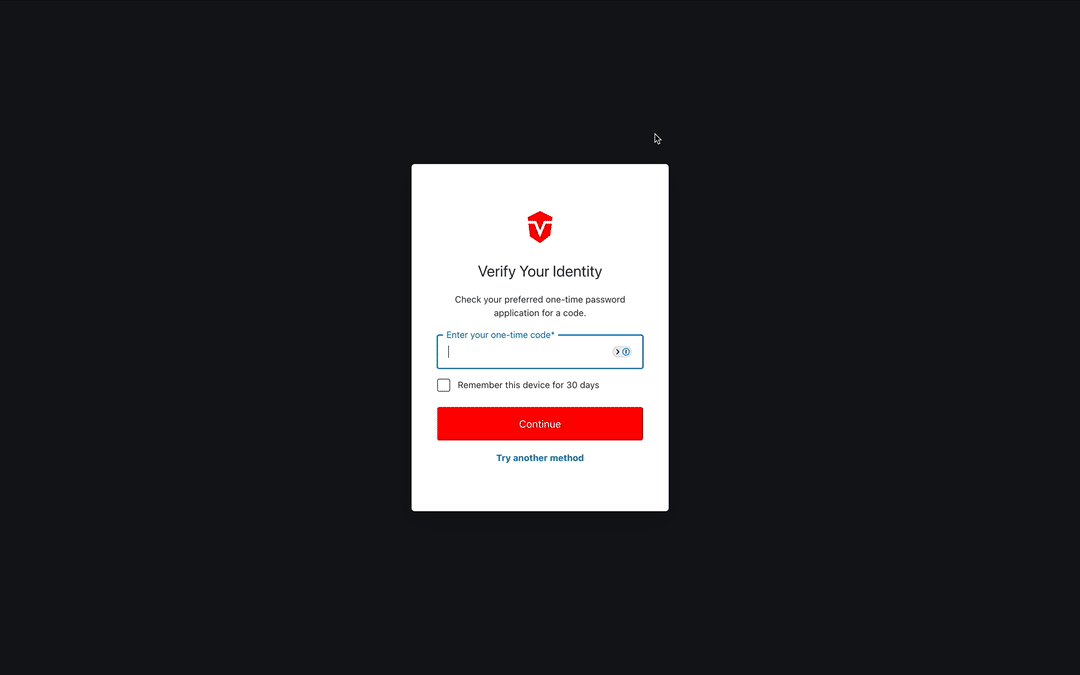
To reset an MFA token, select the kebab icon ( ) in the far-right column that corresponds to the user whose MFA token you would like to reset and then select the Reset MFA token link from the menu. A popup will appear, asking you to confirm that you would like to proceed with the reset. Select the Okay button to continue.
) in the far-right column that corresponds to the user whose MFA token you would like to reset and then select the Reset MFA token link from the menu. A popup will appear, asking you to confirm that you would like to proceed with the reset. Select the Okay button to continue.
You will be redirected to a page where you will be asked to enter a one-time code from your authentication app. Enter your code, then select the Continue button to complete this process.
Lost MFA Login Alternatives
In the event that you have lost access to your MFA authentication app, there are two methods that can be used for accessing your account.
From the Login page, enter and submit your username and password as you normally would. Next, select the Try another method link at the bottom of the Verify Your Identity prompt.
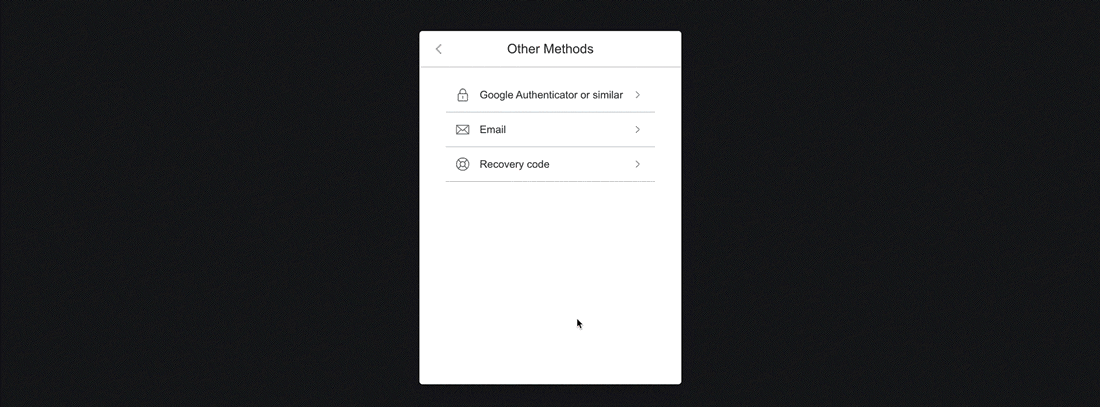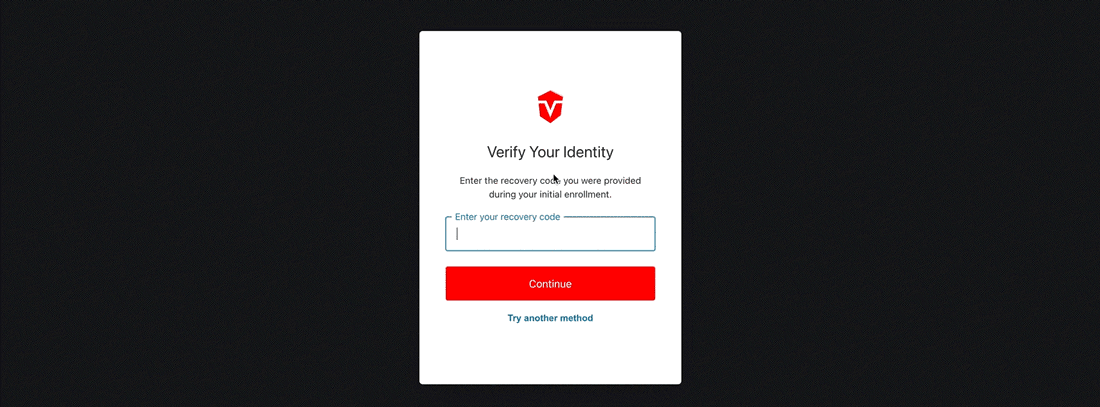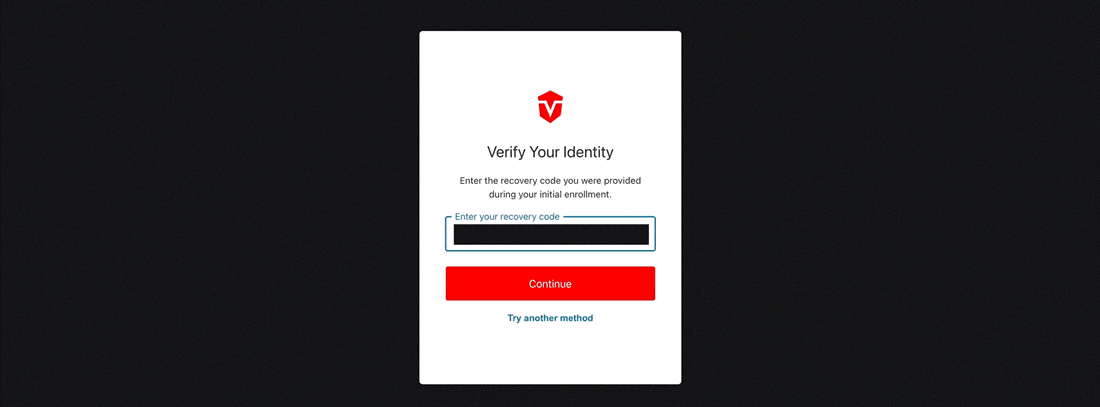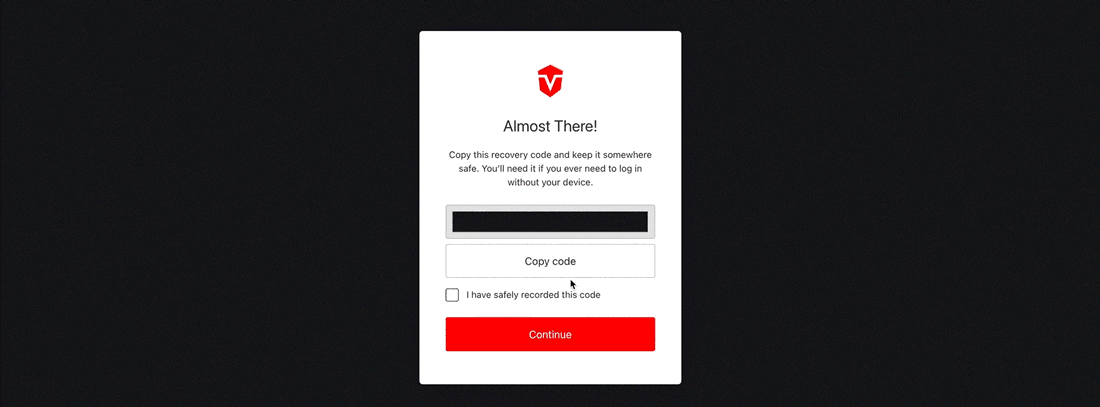
Recovery Code
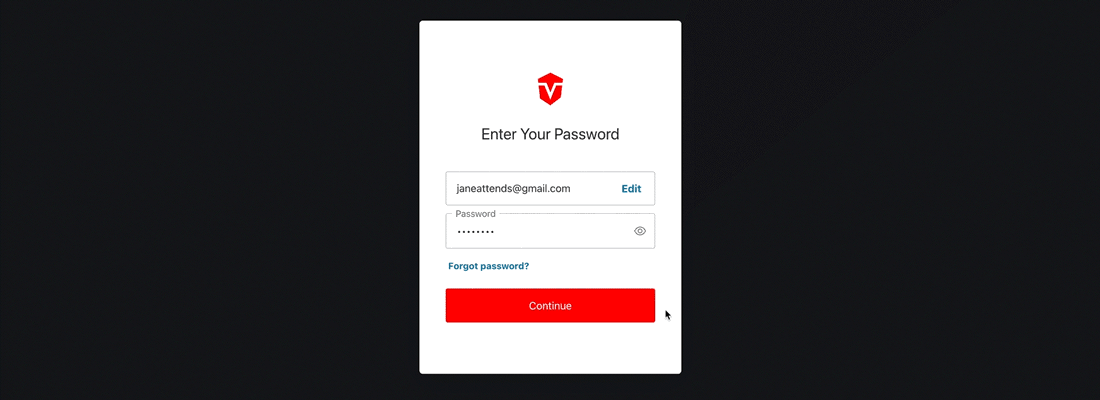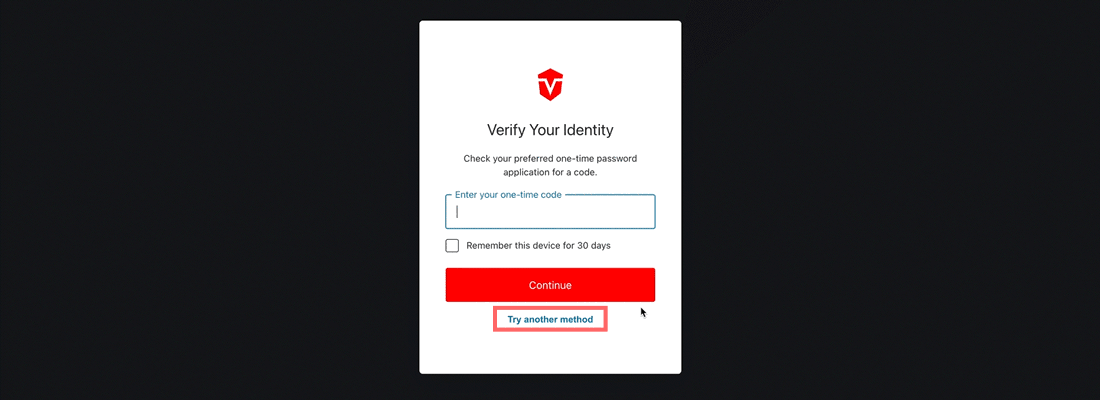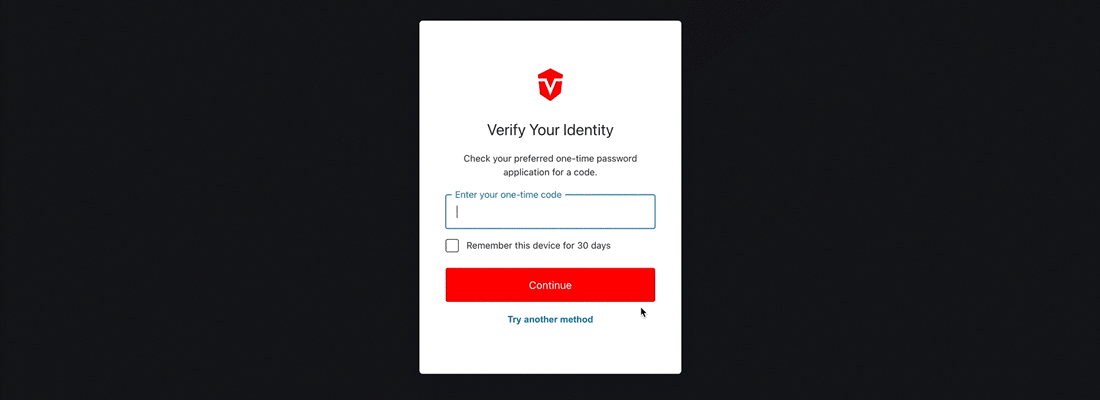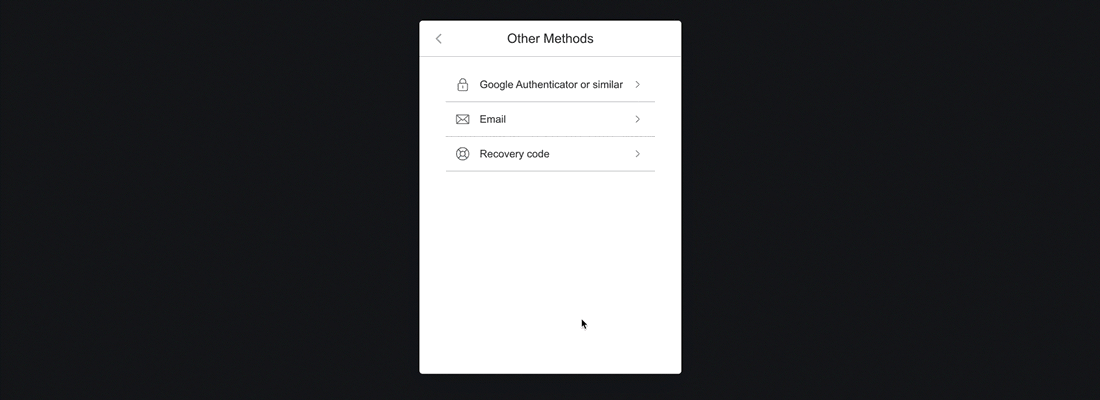
If you have access to your Recovery Code, select the Recovery Code option from the Other Methods menu.
Once you have been redirected, paste your Recovery Code into the provided field, then click the Continue button.
You will be provided with a new Recovery Code. Select the Copy code button to copy the code to your clipboard then save it in a secure place.
Once you've saved your code, check the I have safely recorded this code checkbox, then click the Continue button to complete this process.
Email
In the event that you have lost your Recovery Code, you can have a temporary verification code emailed to you that will allow you to access your account. As a security measure, we recommend only using this method as a last resort.
Select the Email option from the Other Methods menu to begin this process. You will be prompted to enter the code that has been emailed to you. Keep this page open, as you will be returning to it momentarily.
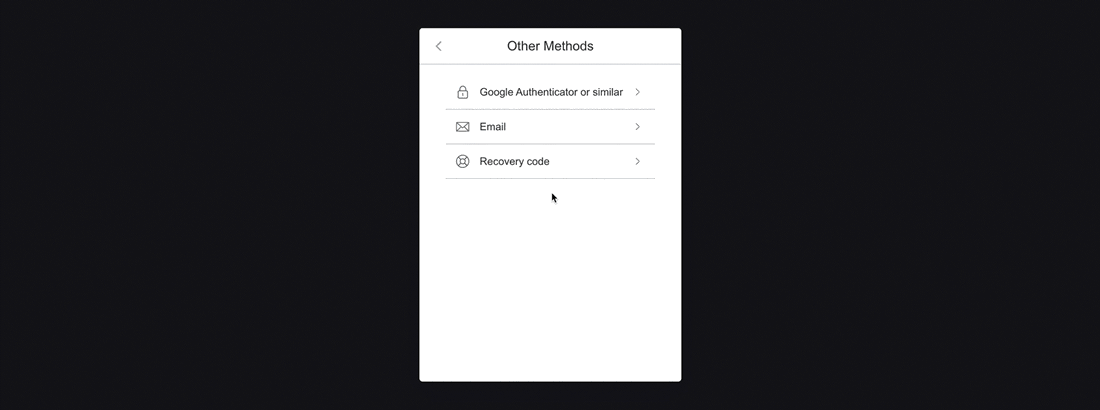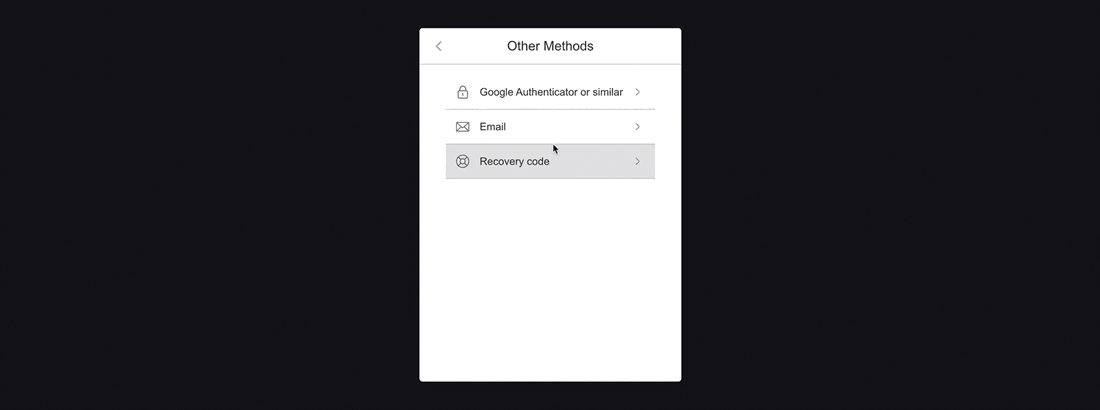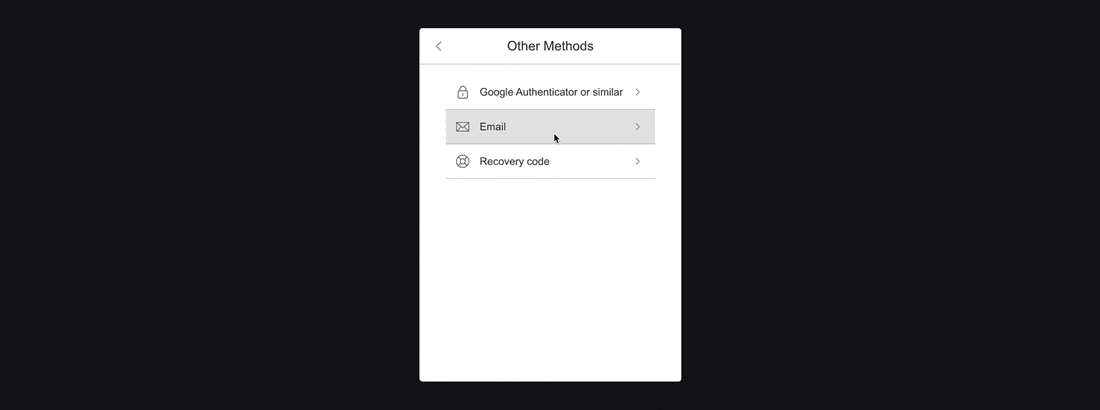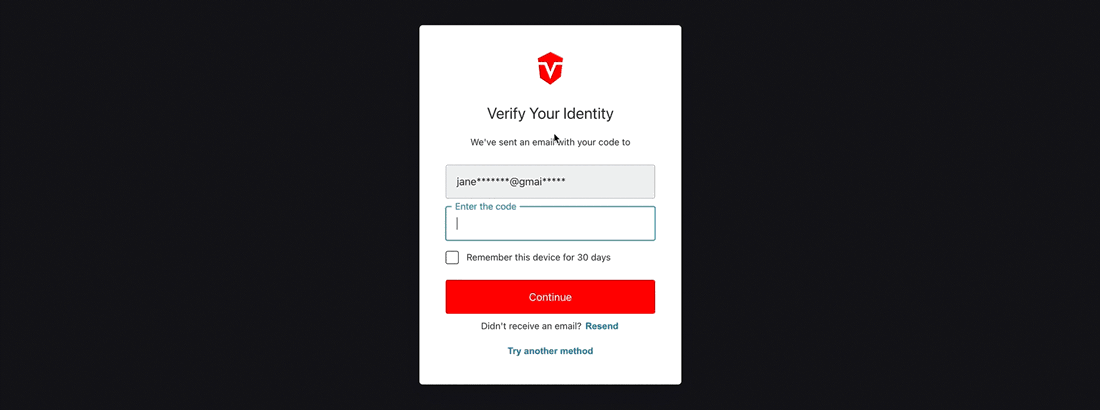
Copy the verification code that has been sent to your email, then return to the verification page in Sevco.

Paste the verification code into the provided field, then select the Continue button to complete this process.
From here, we strongly recommend reaching out to an Admin for your organization and asking them to reset your MFA token for you. If you are an Admin user, ask another Admin user to reset your token for you or reach out to your CSM for assistance doing so if no other Admin user is available to do so.
Enforcing MFA for an Organization
Admin users can enforce MFA Enrollment requirements at the organizational level for all members. Sevco recommends enforcing MFA enrollment at the organizational level to reduce the risk of phishing attempts that could result in stolen credentials.
From the Members page, select the Enforce MFA for all members toggle in the Settings panel.
Logging in with Single Sign-on (SSO Integration)
Admins planning on configuring a Single Sign-on integration for their organization should disable MFA enforcement at the organizational level. Additionally, organization members should also disable MFA enforcement for their accounts.
Admin users can connect their Single sign-on (SSO) integration (i.e. cloud Identity Providers such as Okta or AzureAD) to the Sevco platform using Sevco's SAML Configuration APIs.
Creating an Application
To enable an SSO Integration, your Identity Provider will create an Application. This will require the following configuration information:
Single Sign-on URL:
Replace the0's with your Organization ID
https://sevco.us.auth0.com/login/callback?connection=00000000-0000-0000-0000-000000000000
Audience Restriction (or Entity ID):
urn:auth0:sevco:00000000-0000-0000-0000-000000000000
Additionally, you will need to add a Claim. The claim's Name should equal email and its Value should reflect the naming scheme used by your Identity Provider to qualify a user's email address (i.e. user.email).
Enabling the SSO Integration
After the Application has been created, your Identity Provider will provide an X.509 Certificate as well as a Single Sign-on URL. These will be used when calling the API to enable the SSO Integration.
For additional documentation about Sevco's SAML Configuration APIs, please email us at [email protected].
Updated 11 months ago
