Google Cloud Platform
About Google Cloud Platform
A suite of cloud computing services that runs on the same infrastructure that Google uses internally for its end-user products, such as Google Search, Gmail, Google Drive, and YouTube.
The Data We Collect and How We Use It
The table below lists the fields we collect from Google Cloud Platform and how they map to the fields in our Sevco platform. This data is only used internally; we do not share it with any parties outside of Sevco. Refer to our privacy policy for details.
| Google Cloud Platform Field | Sevco Field |
|---|---|
Id | ID |
Name | Hostnames |
Hostname | Hostnames |
time.now | LastUpdatedTime |
Labels | source-tags |
Google Cloud Platform Service Account Configuration
- Add a source: Follow our instructions to add a Sevco source.

- Provide credentials: You'll be asked to provide source credentials that Sevco will use to connect to Google Cloud Platform:
| Credential or Parameter | Description | Where You Can Find This Value |
|---|---|---|
| project_id | Google Cloud Project ID. If empty the plugin will attempt to pull from all projects accessible by the service account. | To locate your project_id refer to this documentation |
| service_account_json | Service Account JSON key file contents | This information is available in the Google Cloud Console's IAM & Admin → Service Accounts section. For Details refer to this documentation |
-
Create Service Account. For more information on creating a service accounts visit https://cloud.google.com/iam/docs/creating-managing-service-accounts. Create your service account within a project you want imported into Sevco.
-
Set permissions: In Google Cloud Platform, create a new custom role with the following permissions. The role can be in the same project as the service account or in a top-level organization.
compute.instances.get
compute.instances.list
compute.zones.list
resourcemanager.folders.list
resourcemanager.projects.list
resourcemanager.projects.getThe role should look like the following:
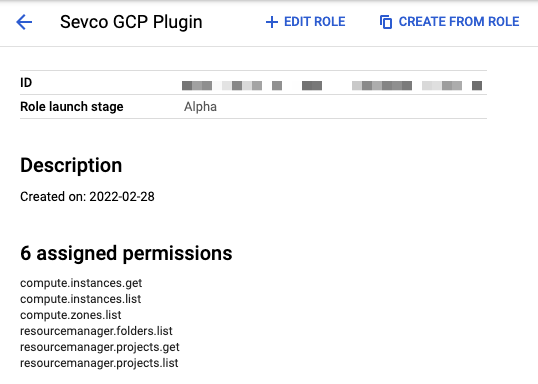
- Add the service account to every project you wish to be imported, or add the service account to a top-level organization with the role created in step 4. This will import compute instances from projects contained within that organization.
Google Cloud Platform OAuth 2.0 Configuration
Permissions
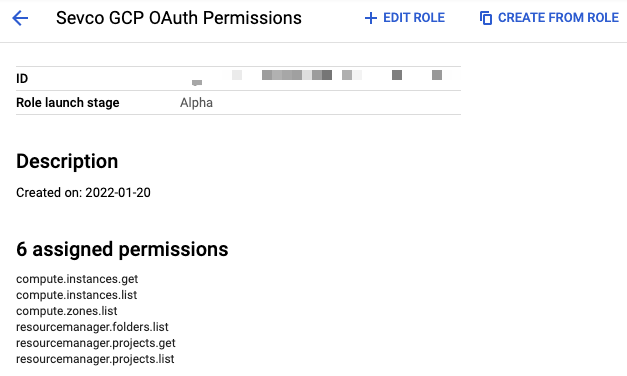
- Create an IAM Role with the following assigned permissions
compute.instances.get
compute.instances.list
compute.zones.list
resourcemanager.folders.list
resourcemanager.projects.list
resourcemanager.projects.getAfter creating your role, it should look like the following:
Assigning your RoleIt is recommended the user performing Oauth 2.0 flow be assigned the role above at a top-level GCP organization. Otherwise not all compute instances will be retrieved. The IAM Role will be inherited by any child projects/folders within your organization.
- Create a new Google Cloud Platform Source and Select OAuth2 configuration. Click Next.

- Read through the click explanation on what happens next. Click Next.

- Enter an Optional Name for this source. Click Activate.

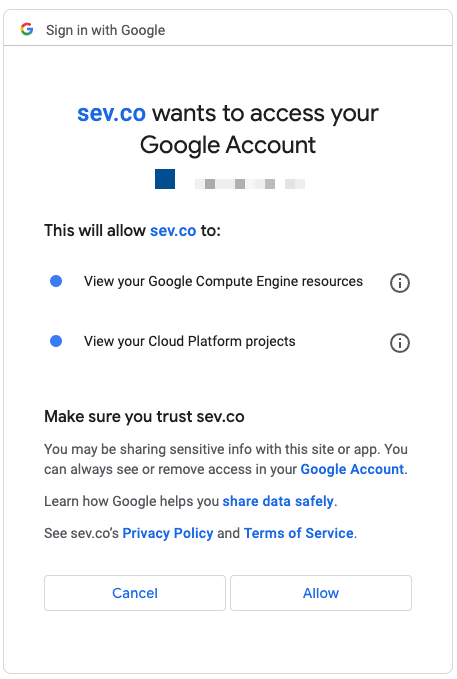
- Select your Google Account to use for this source. and click Allow
Contact Us
If you're having problems configuring an Integration, or if you've found something wrong in this document, please email us at [email protected].
Updated 3 months ago
