Live Vulnerabilities Overview
Overview
Sevco's Live Vulnerabilities unifies your vulnerability data into a single, continuously updated inventory—giving you the context needed to prioritize what actually matters to your business.
Rather than managing fragmented vulnerability reports from multiple scanners, Sevco aggregates, normalizes, and deduplicates findings from across your security stack. Each vulnerability is then mapped to the Asset Graph, connecting it to the devices, users, software, and security controls in your environment. Combined with real-time threat and exploit intelligence from VulnCheck, you get a complete picture of risk—not just technical severity.
What this enables:
Unified visibility – One inventory of all software vulnerabilities, regardless of source, with correlated device, user, and control context
Risk-based prioritization – Score vulnerabilities across severity, exploitability (e.g. CVSS, EPSS, KEV status), and business impact to focus remediation where it reduces the most risk
Actionable intelligence – VulnCheck enrichment surfaces exploit maturity, known threat actor usage, and active exploitation evidence so you can act on emerging threats quickly
Tool rationalization – Compare detection coverage across scanners to identify gaps, eliminate redundancy, and optimize spend
- Run different tools for different asset types while managing everything through a single workflow
- Run multiple tools across all of your assets for the most comprehensive vulnerability assessment.
Vulnerabilities Live Inventory
Accessing the Page
You can access this page by selecting the Live Inventory icon on the Navigation bar and selecting Vulnerabilities from the dropdown.
Vulnerability Inventory Totals
In the top-left corner of the Live Inventory page, you will notice that there are two totals listed for your unified vulnerabilities. The top number represents the total number of distinct vulnerabilities while the bottom number represents the total number of vulnerability instances.
- Distinct Vulnerabilities – A unique vulnerability, counted once regardless of how many assets it affects. CVE-2024-1234 is one distinct vulnerability whether it's on one device or 500. Each distinct vulnerability is only counted once and is included in the Vulnerability Inventory List.
- Vulnerability Instances – Individual occurrences of a vulnerability on specific assets. If CVE-2024-1234 is found on 50 devices, that's 50 instances. Each instance of a distinct vulnerability is factored into the total vulnerability instances count, resulting in a total that is often much higher than the distinct-vulnerability total.

Vulnerability Inventory List
The Inventory List provides a real-time snapshot of all the software vulnerabilities reported by your Source integrations. Each row represents a unique software vulnerability identified in your environment.
An overview of your vulnerability prioritization metrics is displayed in the columns. This includes:
- Overall severity score
- CVSS scores – a numerical rating from 0.0-10.0 that indicates the severity of a known software vulnerability (Learn more)
- EPSS probability – a score from 0%-100% that indicates the likelihood of a specific vulnerability (CVE) being exploited within the next 30 days (Learn more)
- Known Exploited Vulnerability (KEV) status – indicates if a vulnerability is included in CISA or VulnCheck's KEV catalog (Learn more)
-
- CISA KEV is the U.S. government's official, prioritized list of vulnerabilities actively being exploited
-
- VulnCheck KEV is a third-party catalog that includes CISA's list and additional vulnerabilities, typically updated more frequently with richer exploit details like POCs
- Associated CVE – a unique identifier for a publicly-disclosed cybersecurity vulnerability. The CVE database is maintained by The MITRE Corporation. (Learn more)
- Number of devices impacted by the vulnerability
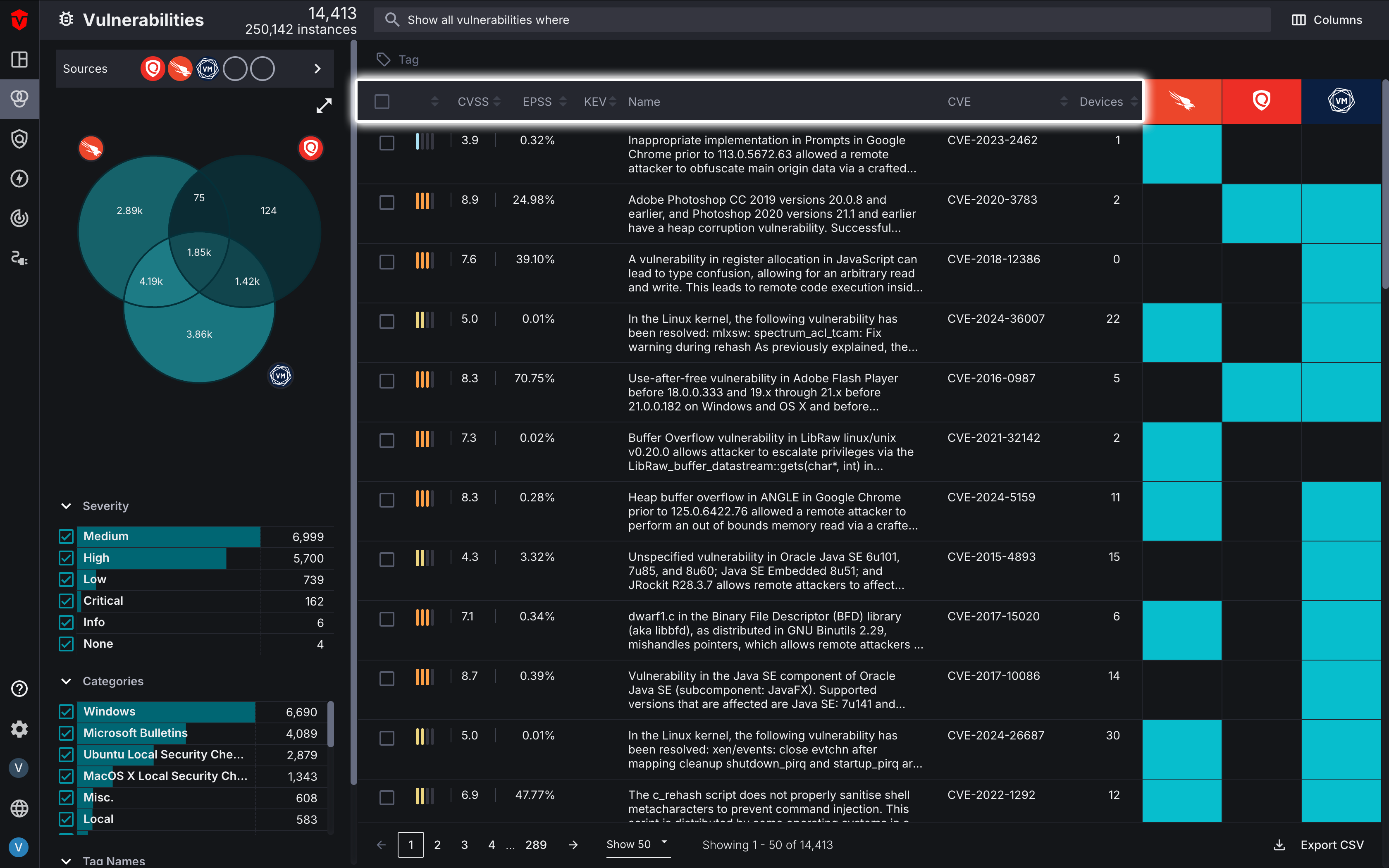
The heat map on the right indicates whether or not a Source integration has detected a software vulnerability:
- Blue means the Source has detected it
- Black means the Source has not detected it
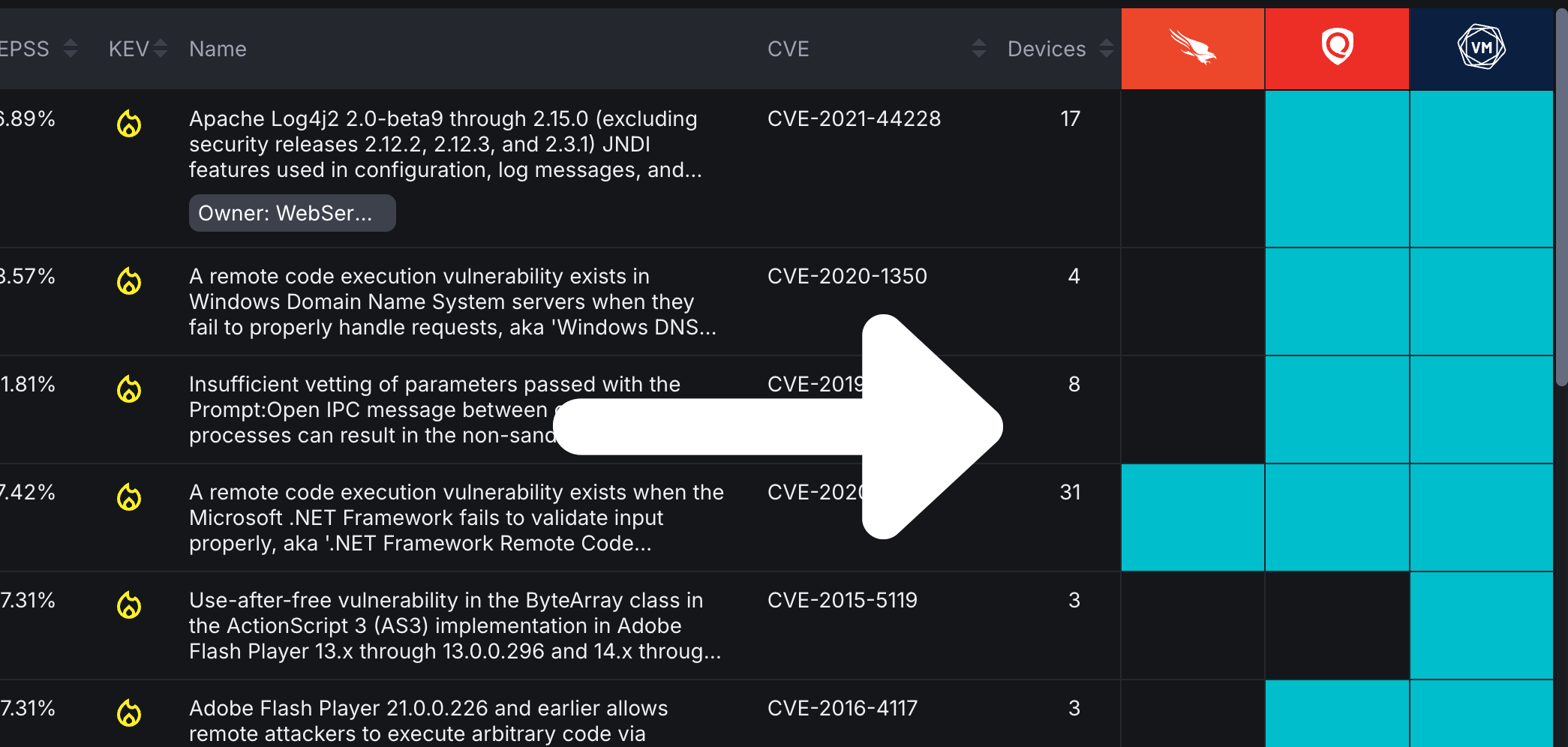
Select a row to reveal more information about that software vulnerability:
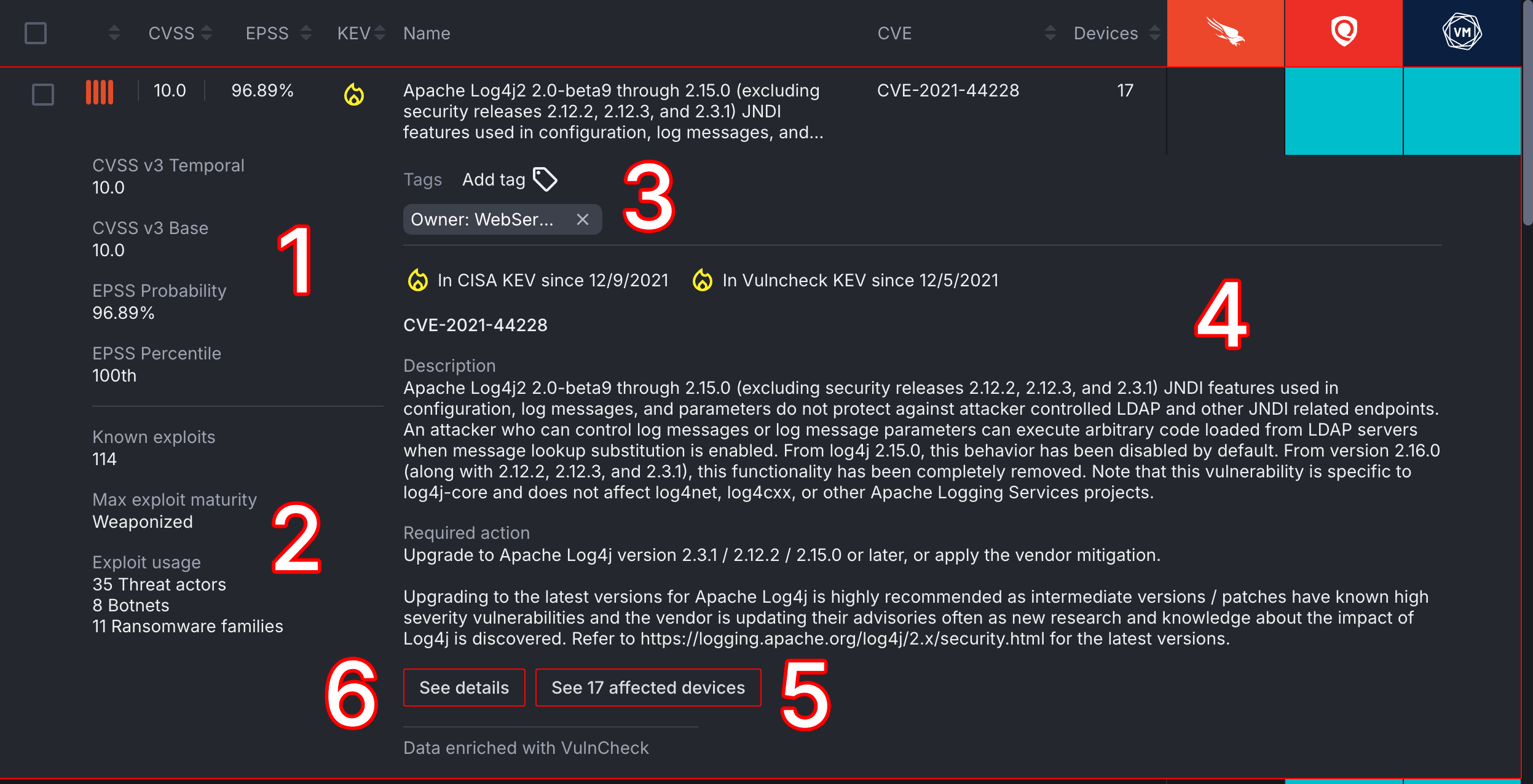
- The left column provides more in-depth information about a software vulnerability's CVSS scores as well as its EPSS probability and percentile.
- Information about known exploits, their maturity (i.e., Weaponized), and usage is also listed in the left column.
- The Tags section allows you to manage what tags are associated with a software vulnerability.
- Information about software vulnerabilities is enriched with data from VulnCheck, providing you with a description of the vulnerability and a solution for remediating it.
- To view devices impacted by a software vulnerability, select the See affected devices button.
- Select the See details button to access a software vulnerability's Vulnerability Details page.
Venn Diagram and Filters
Like the Device and User Live Inventory pages, this page offers the same Filtering and Venn Diagram tools to help you identify specific software vulnerabilities.
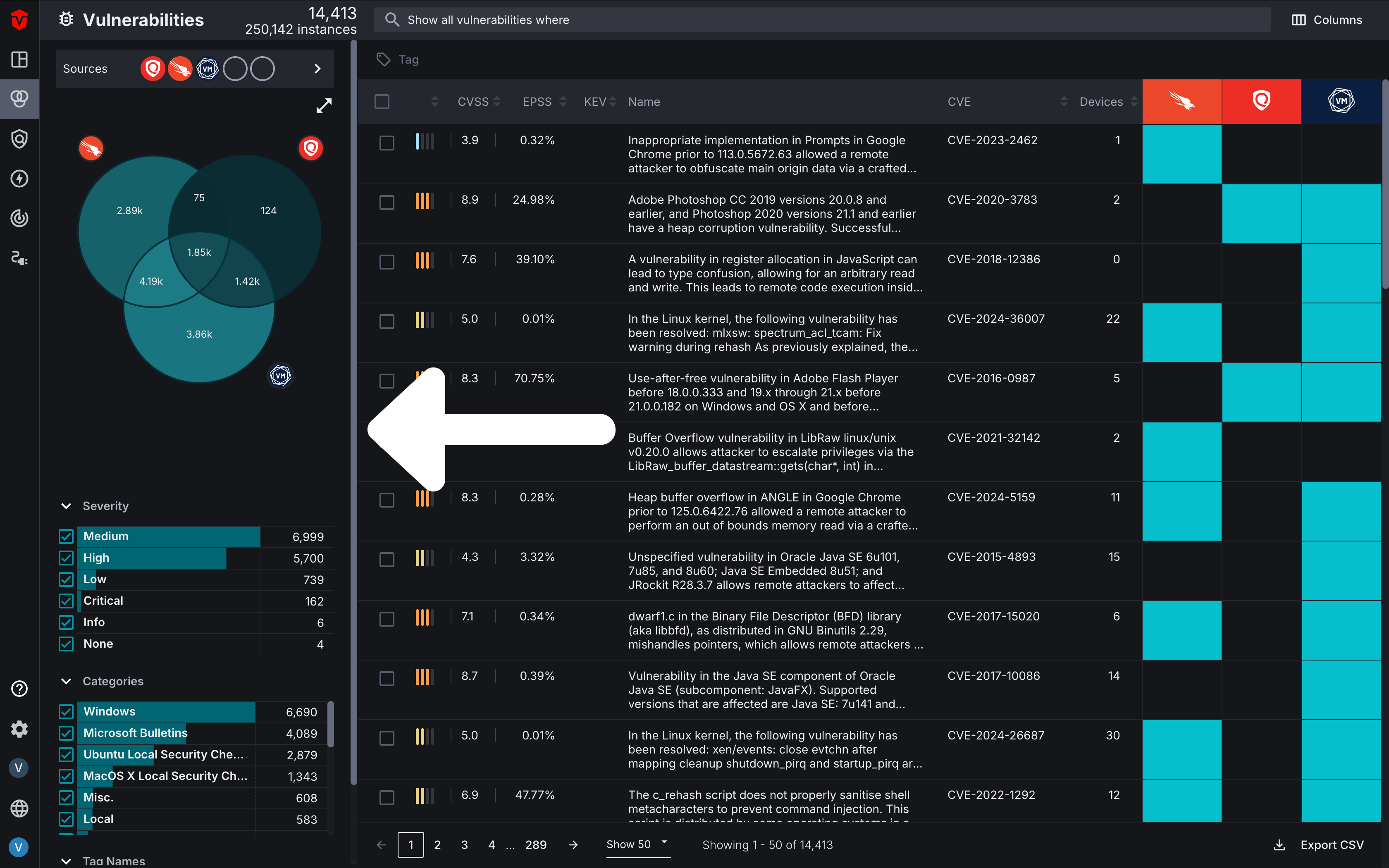
Query Builder
The Query Builder is a powerful tool that allows you to search for specific software vulnerabilities using criteria defined in a query associated with any other asset attribute. For example, you may wish to run a query that displays Critical software vulnerabilities impacting Windows Server devices that are being accessed by domain admins in Microsoft AD. Regardless of what query you are running, the query builder is the easiest way to gain insight into how software vulnerabilities are impacting specific segments of your asset environment.
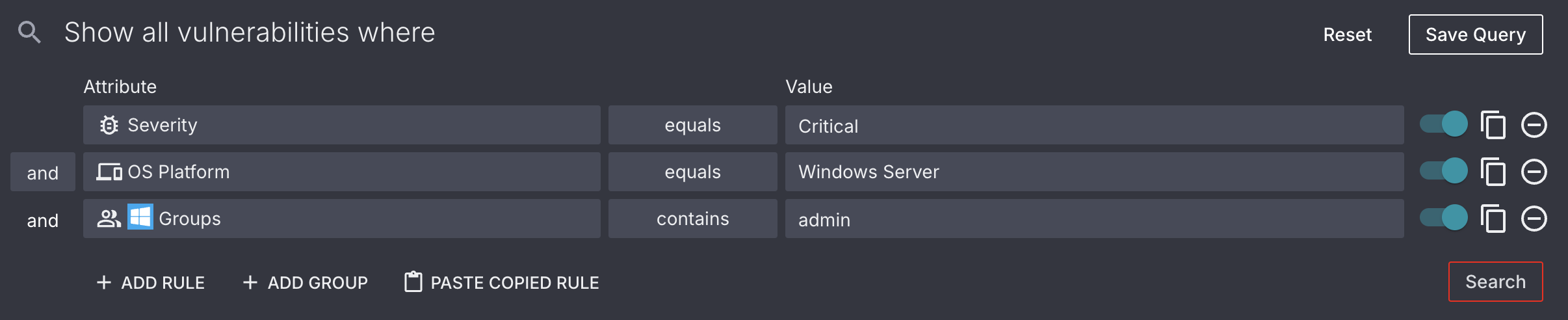
Vulnerability Details
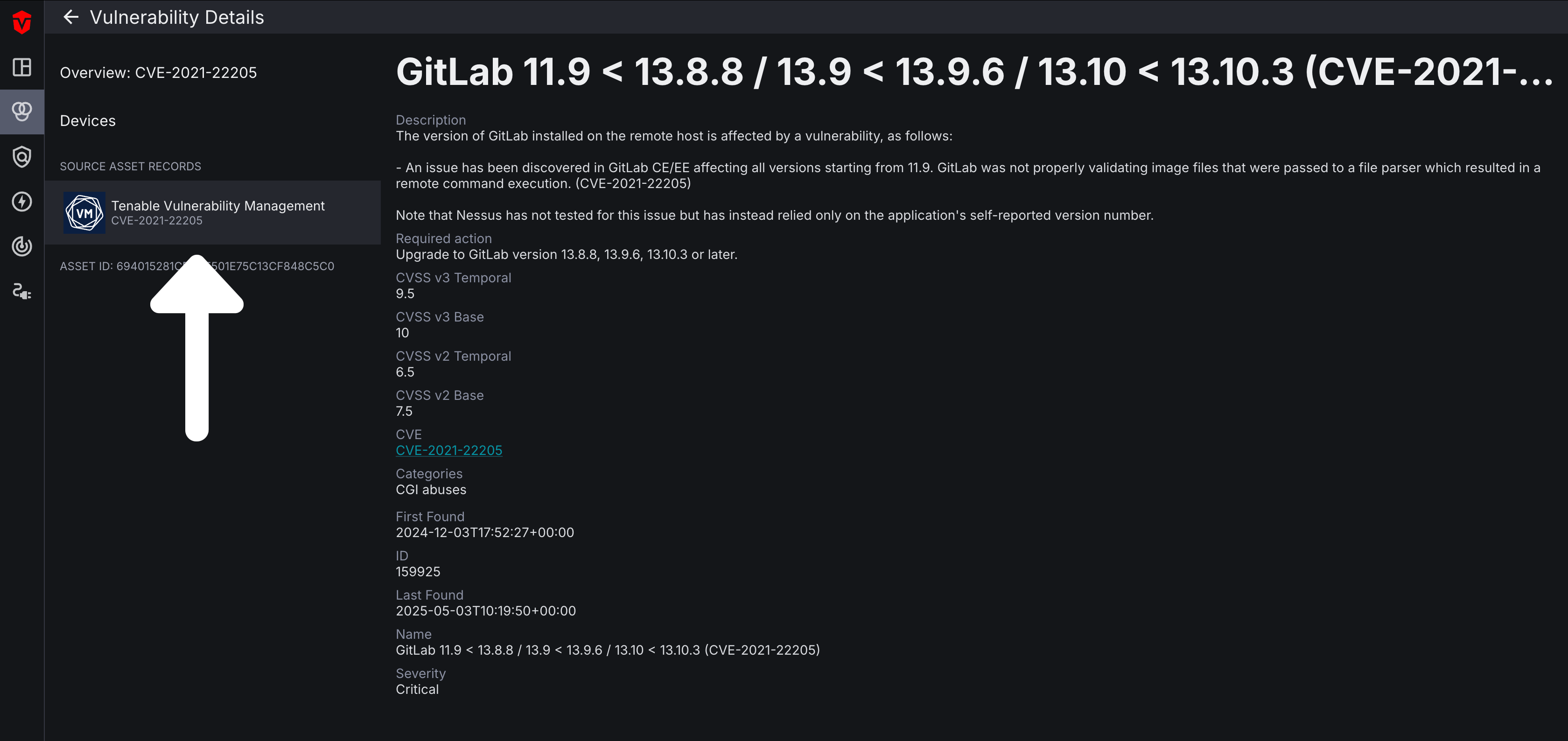
In addition to the information found on the Vulnerabilities Live Inventory page, you can also view additional information about a vulnerability on its Vulnerability Details page.
This page can be accessed by selecting a software vulnerability's name or the See details button in its dropdown.
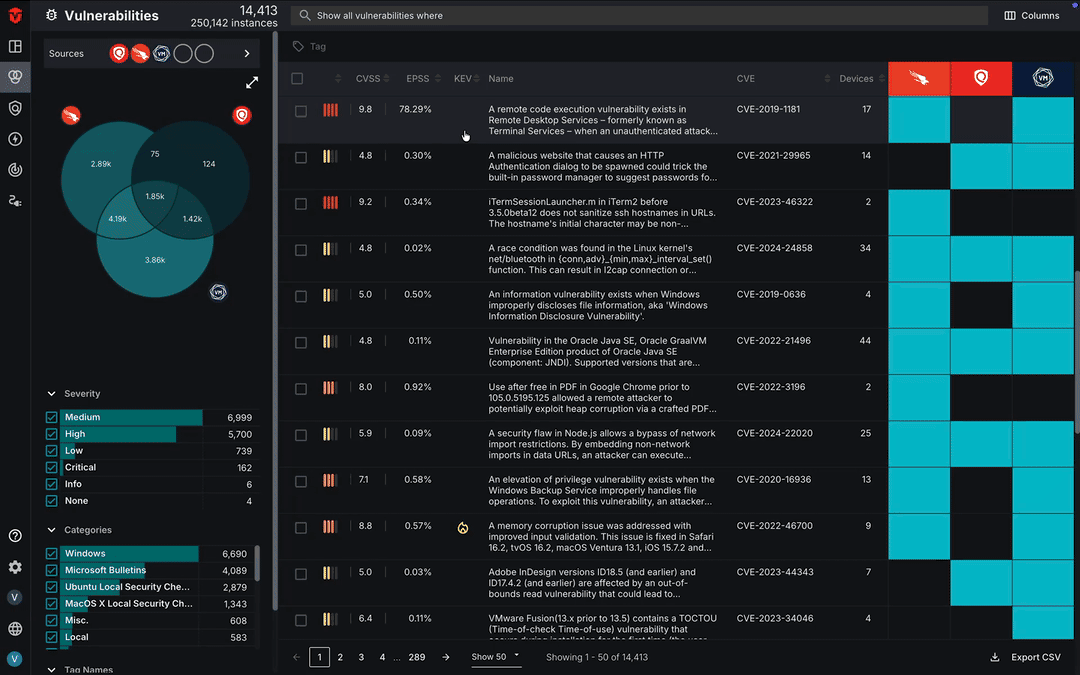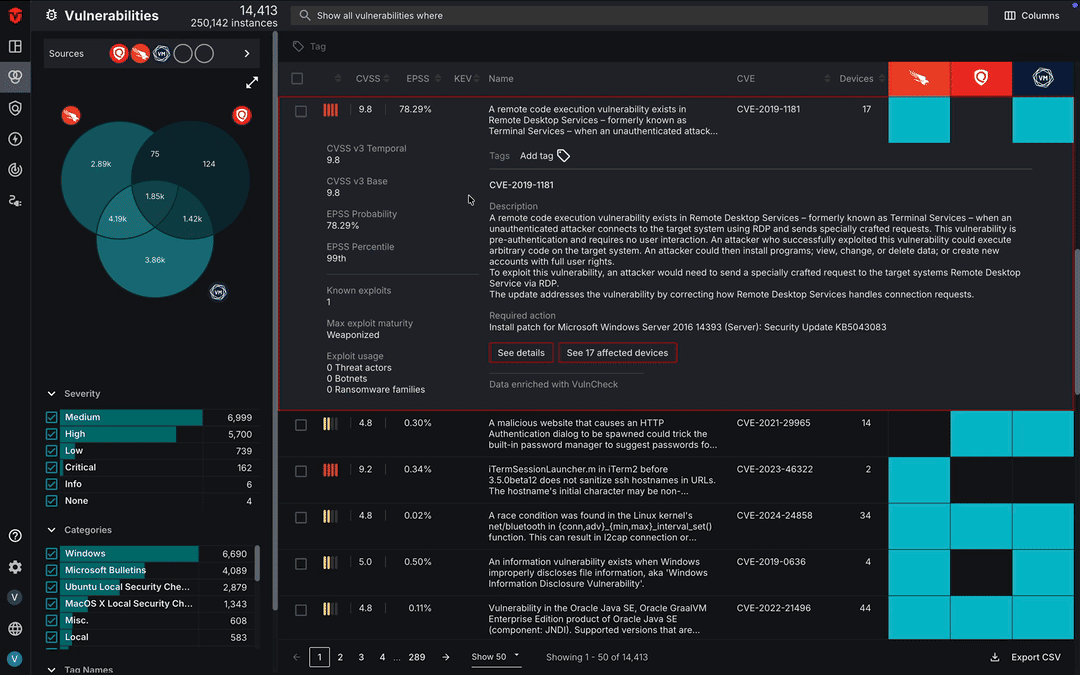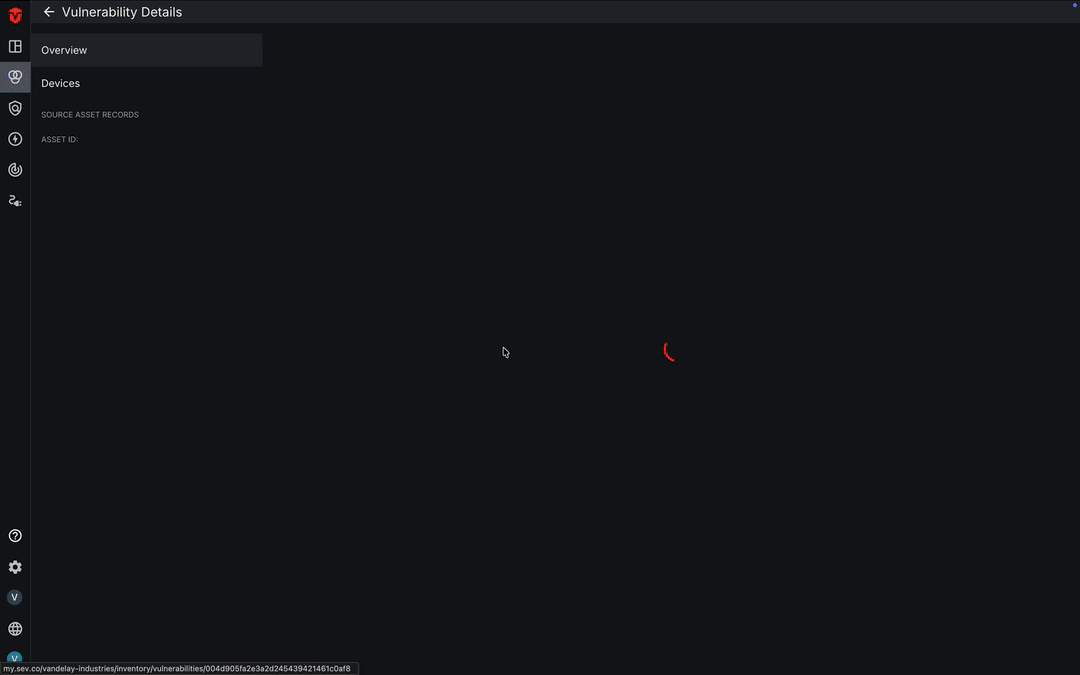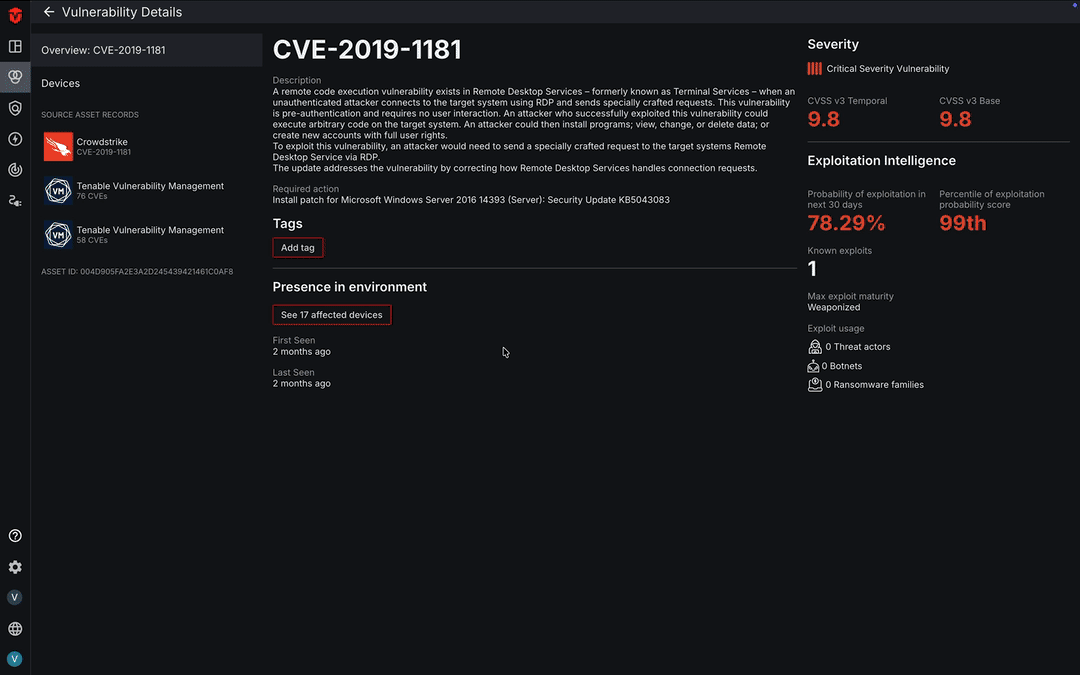
Unified Vulnerability Details
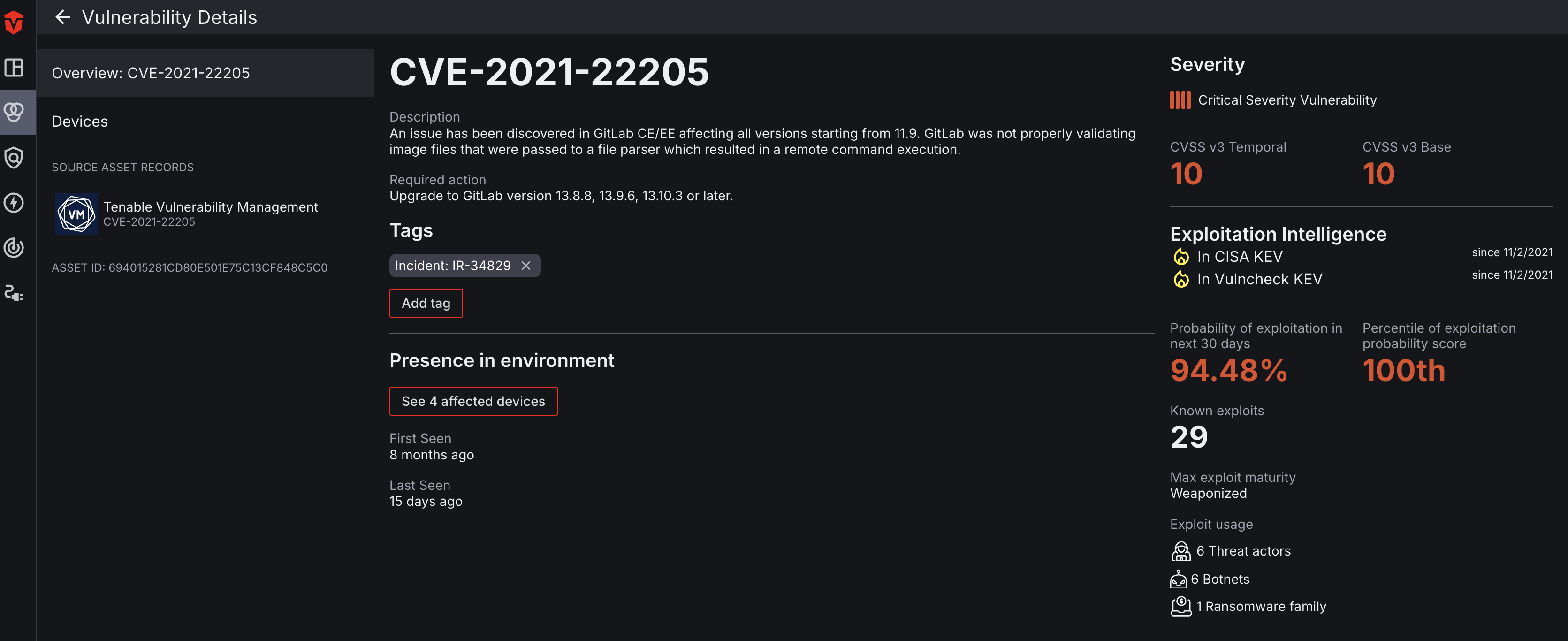
The Vulnerability Details page contains VulnCheck data that provides additional information about the software vulnerability, such as a description of it and the required action to remediate it. You can also find information about its presence in your environment such the number of devices impacted by it as well as when it was first and last seen.
The right panel of the page takes data from all of your vulnerability Sources and creates an overview of a vulnerability's risk factors. This includes information about its severity such as CVSS scores, number of known exploits, exploit maturity, how the vulnerability is being exploited (exploit usage), and the probability of it being exploited.
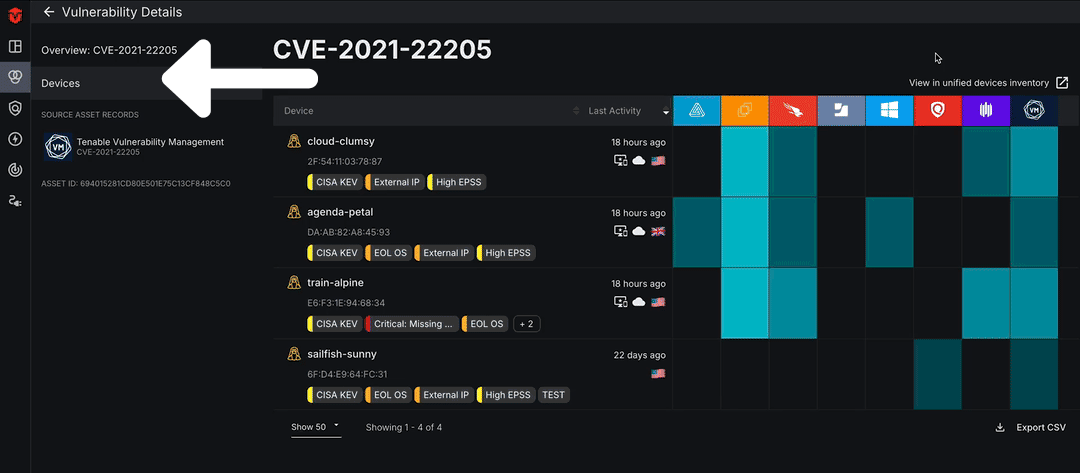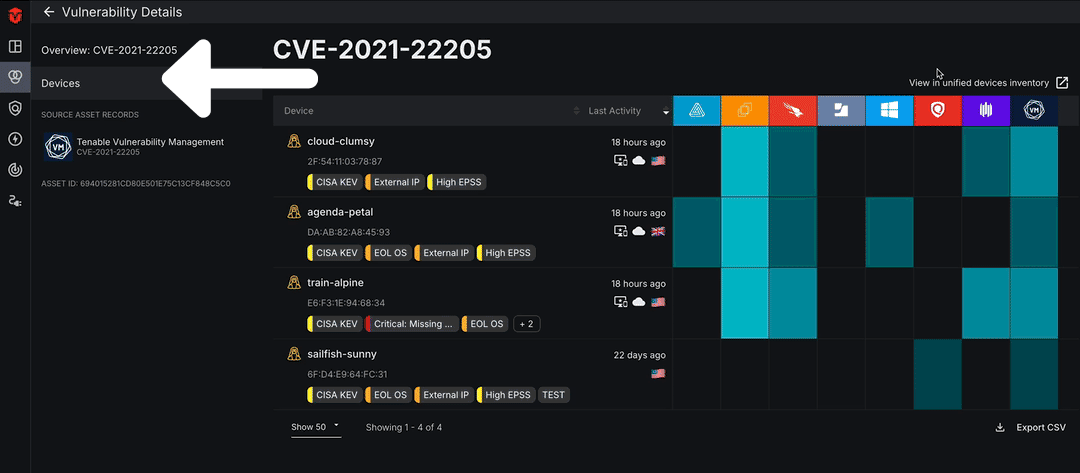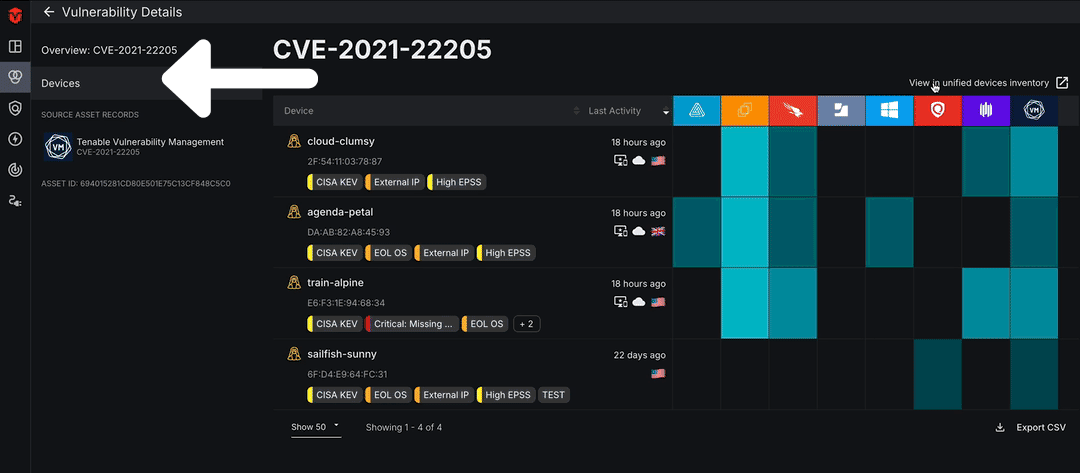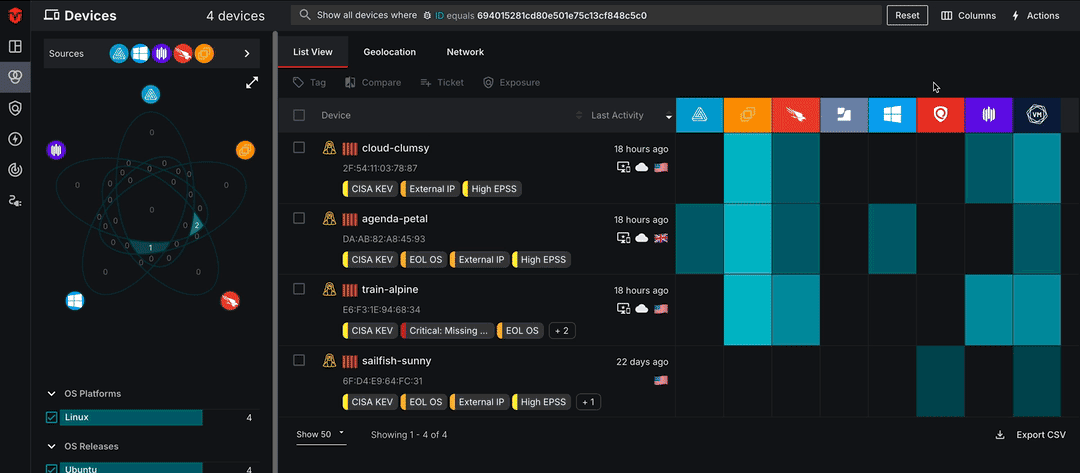
Click the Devices tab on the left menu to view all devices affected by a vulnerability. From there, you can select the See affected devices button to view all devices with the software vulnerability on the Device Live Inventory page.
Source Details for Vulnerabilities
On the left menu of the page, you can view information about a software vulnerability as it is reported by each of your Sources. Select a Source Asset Record to view data reported directly from a specific Source.
Asset Processing Pipeline
The vulnerability Asset Processing Pipeline graph provides a visual representation of all of your Source vulnerability instances and how they are processed by Sevco's Asset Correlation Engine (ACE) into distinct live vulnerabilities and live vulnerability instances. You can access this graph by selecting the Source breakdown dropdown in the bottom-left corner of the Vulnerability Instances section of the Dashboard page.
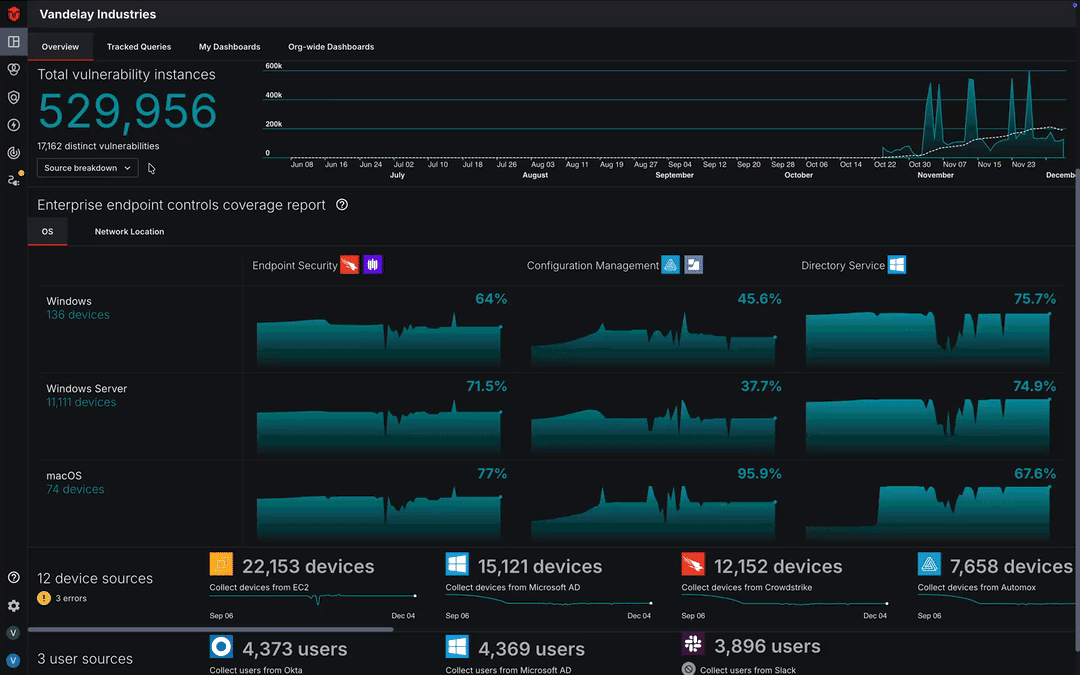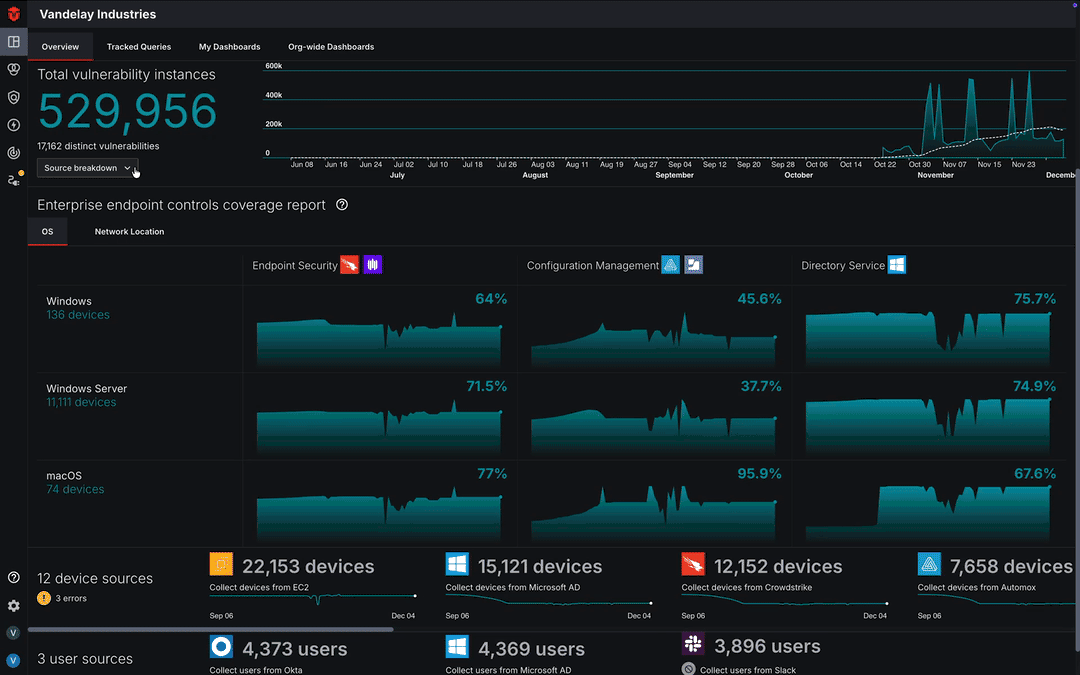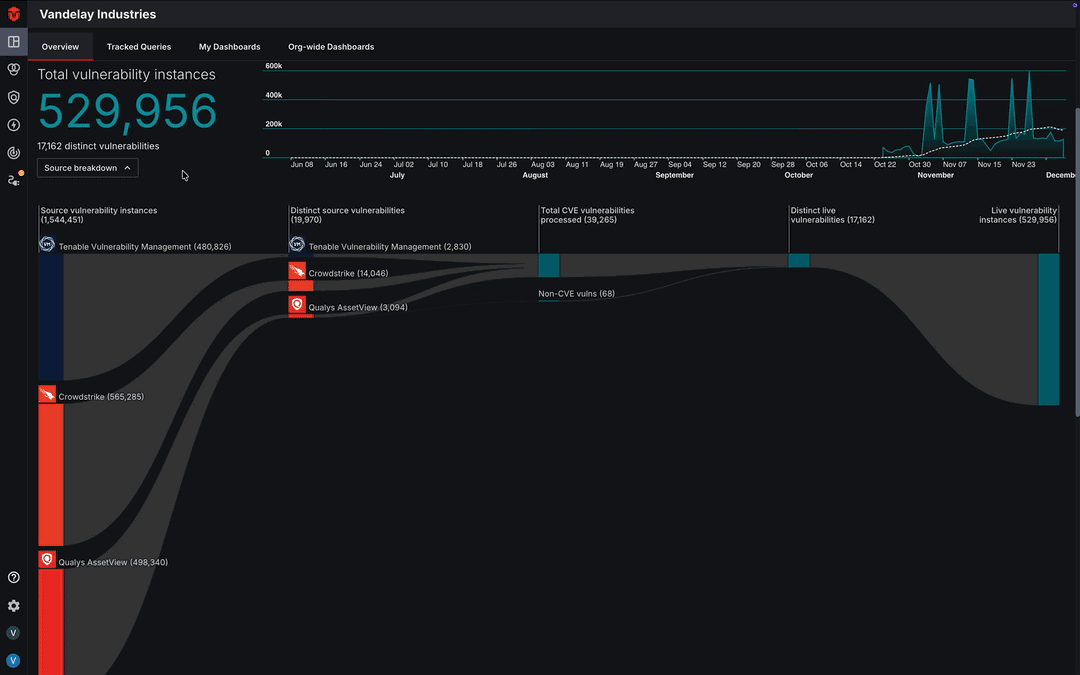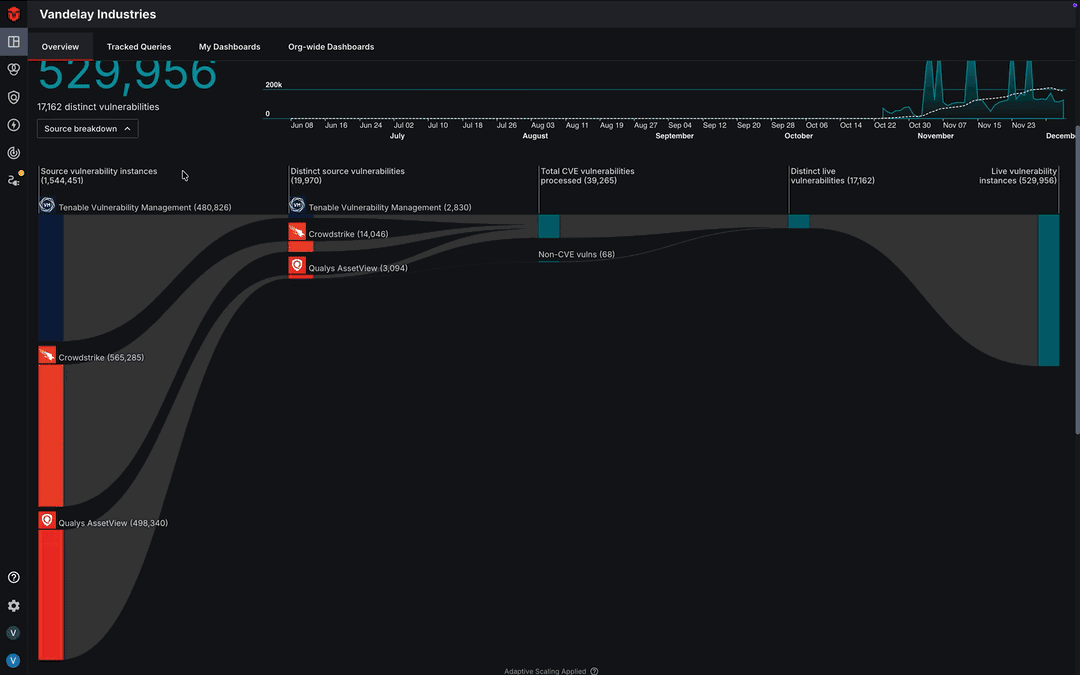
Learn more about the Asset Processing Pipeline
Source Vulnerability Inventory
The Vulnerability Inventory page is a type of Source Inventory page. These pages are integration-specific and only display vulnerability data from a single vulnerability Source integration-type. Vulnerability Inventory pages can be used to search for and monitor vulnerabilities associated with a Source. Additionally, you can also review information about a vulnerability Source's health (Status) and reconfigure it as-needed.
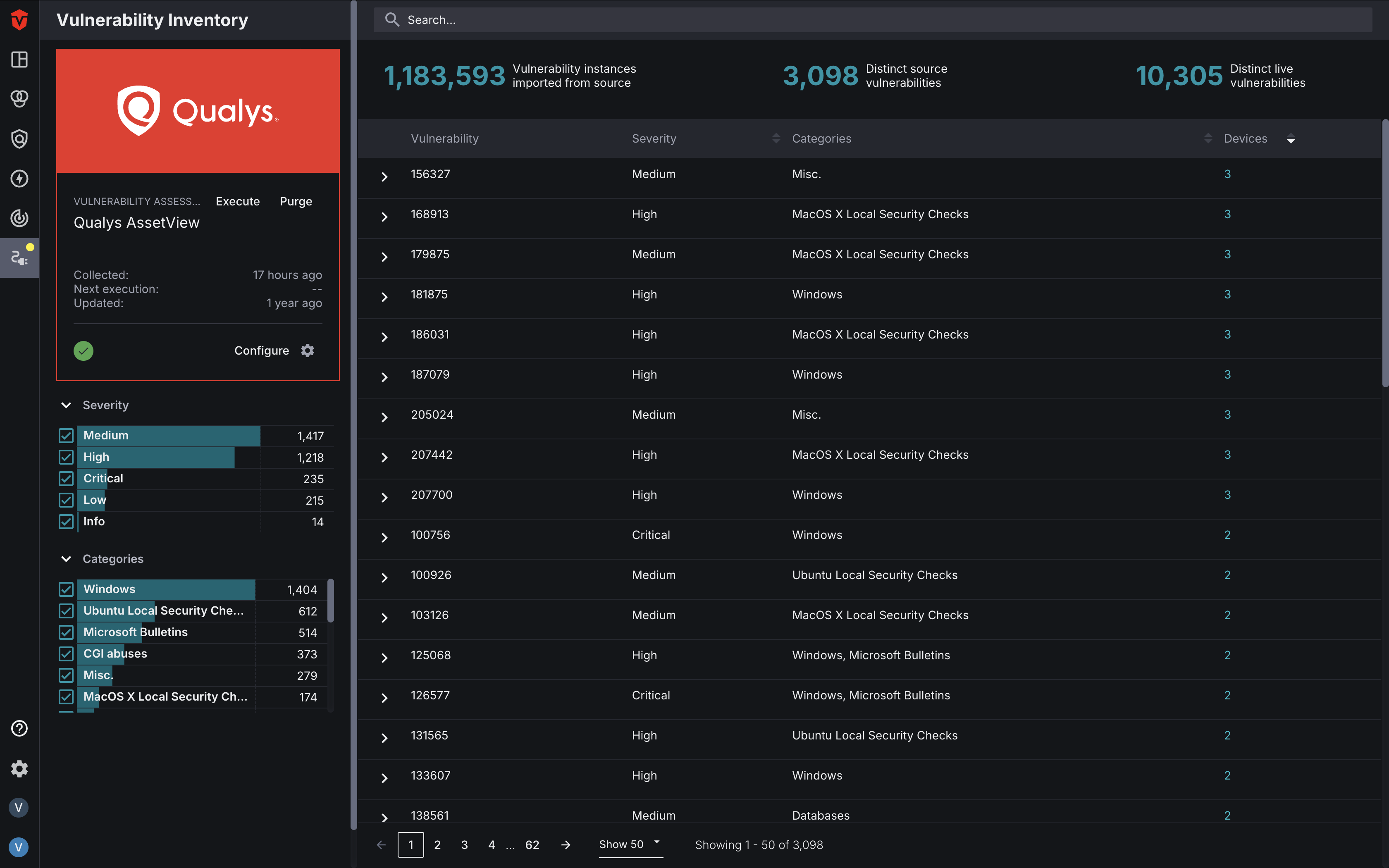
Learn more about about Vulnerability Inventory pages and Source Inventory pages more broadly.
Updated about 2 months ago
